
Email Protection | Cloudflare

Email Protection | Cloudflare
The Cisco Email Security Difference
Customers of all sizes face the same daunting challenge: email is simultaneously the most important business communication tool and the leading attack vector for security breaches. Cisco® Email Security enables users to communicate securely and helps organizations combat Business Email Compromise (BEC), ransomware, advanced malware, phishing, spam, and data loss with a multilayered approach to security.
Product overview
Cisco Email Security includes advanced threat protection capabilities to detect, block, and remediate threats faster; prevent data loss; and secure important information in transit with end-to-end encryption.
With Cisco Email Security customers can:
● Detect and block more threats with superior threat intelligence from Talos™, our threat research team.
● Combat ransomware hidden in attachments that evade initial detection with Cisco Advanced Malware Protection (AMP) and Cisco Threat Grid.
● Drop emails with risky links automatically or block access to newly infected sites with real-time URL analysis to protect against phishing and BEC.
● Prevent brand abuse and sophisticated identity-based email attacks with Cisco Domain Protection (CDP) and Cisco Advanced Phishing Protection (CAPP) services.
● Protect sensitive content in outgoing emails with Data Loss Prevention (DLP) and easy-to-use email encryption, all in one solution.
● Provide user behavior training with Cisco Security Awareness to help users work smarter and safer.
● Gain maximum deployment flexibility with a cloud, virtual, on-premises, or hybrid deployment or move to the cloud in phases.
Features and benefits
Today’s email security threats consist of ransomware, advanced malware, BEC, phishing, and spam. Cisco Email Security technology blocks threats so that companies receive only legitimate messages. Cisco uses multiple layers to provide the utmost in comprehensive email security, incorporating preventive and reactive measures to strengthen your defense. Table 1 summarizes the major capabilities of our email security solutions.
Table 1. Main capabilities
Feature | Benefit |
Global threat intelligence | Get fast, comprehensive email protection backed by Talos, one of the largest threat detection networks in the world. Talos provides broad visibility and a large footprint, including: ● 600 billion emails per day ● 16 billion web requests per day ● 1.5 million malware samples Talos provides a 24-hour view into global traffic activity. It analyzes anomalies, uncovers new threats, and monitors traffic trends. Talos helps prevent zero-hour attacks by continually generating rules that feed updates to customers’ email security solutions. These updates occur every three to five minutes, delivering industry-leading threat defense. |
Reputation filtering | Block unwanted email with reputation filtering, which is based on threat intelligence from Talos. For each embedded hyperlink, a reputation check is performed to verify the integrity of the source. Websites with known bad reputations are automatically blocked. Reputation filtering stops 90 percent of spam before it even enters your network, allowing the solution to scale by analyzing a much smaller payload. |
Spam protection | Spam is a complex problem that demands a sophisticated solution. Cisco makes it easy. Cisco Email Security blocks unwanted emails using a multilayered scanning architecture delivering the highest spam catch rate of greater than 99 percent, with a false-positive rate of a less than a one in one million. The antispam functionality in Cisco Email Security uses the Cisco Context Adaptive Scanning Engine (CASE). This engine examines the complete context of a message, including what content the message contains, how the message is constructed, who is sending the message, and where the call to action of the message takes you. By combining these elements, Cisco Email Security stops the broadest range of threats with industry-leading accuracy. |
Forged email detection | Forged email detection protects against BEC attacks focused on executives, who are considered high-value targets. Forged-email detection helps you block these customized attacks and provides detailed logs on all attempts and actions taken. |
Cisco Advanced Phishing Protection | CAPP stops identity deception–based attacks such as social engineering, imposters, and BEC by combining global Cisco Talos threat intelligence with local email intelligence and advanced machine learning techniques to model trusted email behavior on the Internet, within organizations and between individuals. ● Integrates machine learning techniques to drive daily model updates, maintaining a real-time understanding of email behavior to stop identity deception. ● Combines rapid Domain Message Authentication Reporting and Conformance (DMARC), advanced display name protection, and look-alike domain imposter–driven detection to stop BEC attacks. ● Models account takeover threat behavior to block attacks originating from compromised email accounts. ● Deploys as a lightweight sensor via the cloud or on-premises in the customer’s environment as a hosted Virtual Machine (VM) of choice or bare-metal installs. Please refer to Table 7 for virtual machine hardware specifications. A cloud-based sensor is provisioned as part of Cisco Cloud Email Security deployment. ● Supports dual-delivery mode. In this mode, the sensor accepts copies of email messages over Simple Mail Transfer Protocol (SMTP) and extracts metadata in a streaming fashion. |
Cisco Domain Protection | CDP for external email helps prevent phishing emails from being sent using a customer domain(s). It automates the process of implementing the DMARC email authentication standard to better protect employees, customers, and suppliers from phishing attacks using a customer domain(s). This protects the customers’ brand identity as well as increases email marketing effectiveness by reducing phishing messages from reaching inboxes. |
Virus defense | By offering a high-performance virus scanning solution integrated at the gateway, Cisco Email Security provides a multilayered, multivendor approach to virus filtering. |
Graymail detection and safe unsubscribe | Graymail consists of marketing, social networking, and bulk messages. The graymail detection feature precisely classifies and monitors graymail entering an organization. An administrator can then take appropriate action on each category. Often graymail has an unsubscribe link where end users can indicate to the sender that they would like to opt out of receiving such emails. Since mimicking a unsubscribe mechanism is a popular phishing technique, users should be wary of clicking these unsubscribe links. The safe unsubscribe solution provides: ● Protection against malicious threats masquerading as unsubscribe links. ● A uniform interface for managing all subscriptions. Better visibility for email administrators and end users into such emails. |
Cisco Advanced Malware Protection and Cisco Threat Grid | AMP and Threat Grid provide file reputation scoring and blocking, file sandboxing, and file retrospection for continuous analysis of threats. Users can block more attacks, track suspicious files, mitigate the scope of an outbreak, and remediate quickly. Cisco Email Security also integrates with AMP for Endpoints. AMP for Endpoints shares threat intelligence across a customer’s entire environment, unifying security across endpoints, network, email, the cloud, and the web. Through these integrations, AMP automatically correlates files, telemetry data, behavior, and activity to proactively defend against advanced threats across all possible vectors. Mailbox Auto-Remediation for Office 365 customers helps remediate breaches faster and with less effort. Customers simply set their email security solution to take automatic actions on those infected emails. Customers can purchase an additional license to deploy their AMP system completely on-premises with the AMP private cloud. This, along with Threat Grid, brings the entire AMP offering completely on-premises. |
URL-related protection and control | Users are protected against malicious URLs with URL filtering, scanning of URLs in attachments, and managed (shortened) URLs. Appropriate policies are applied to the messages based on the reputation or category of the URLs. |
Outbreak filters | Outbreak filters defend against emerging threats and blended attacks. They can issue rules on any combination of six parameters, including file type, file name, file size, and URLs in a message. As Talos learns more about an outbreak, it can modify rules and release messages from quarantine accordingly. Outbreak filters can also rewrite URLs linked in suspicious messages. When clicked, the new URLs redirect the recipient through the Cisco Web Security proxy. The website content is then actively scanned, and outbreak filters will display a block screen to the user if the site contains malware. |
Web interaction tracking | Web interaction tracking is a fully integrated solution that allows IT administrators to track the end users who click on URLs that have been rewritten by Cisco Email Security. Reports show: ● Top users who clicked on malicious URLs. ● The top malicious URLs clicked by end users. Date and time, rewrite reason, and action taken on the URLs. |
Data security for sensitive content in outgoing emails | Cisco Email Security offers effective DPL and email encryption. Centralized management and reporting simplifies data protection. DLP Protect outbound messages with Cisco Email Security DLP. Comply with industry and government regulations worldwide and prevent confidential data from leaving your network. Choose from an extensive policy library of more than 100 expert policies covering government, private sector, and company-specific regulations. The predefined DLP policies are included with Cisco Email Security and simplify the application of content-aware outbound email policy. Remediation choices include encrypting, adding footers and disclaimers, adding Blind Carbon Copies (BCCs), notifying, and quarantining. For companies needing a complex custom policy, the building blocks of the predefined policies are readily available to make the process quick and easy. Encryption Give senders control of their content, even after messages have been sent. With email encryption, senders don’t fear mistyped recipient addresses, mistakes in content, or time-sensitive emails because they can always lock a message. The sender of an encrypted message receives a read receipt once a recipient opens a message, and highly secure replies and forwards are automatically encrypted to maintain end-to-end privacy and control. There is no additional infrastructure to deploy. For enhanced security, message content goes straight from your gateway to the recipient, and only the encryption key is stored in the cloud. Meet encryption requirements for regulations such as the Payment Card Industry Data Security Standard (PCI DSS), the Health Insurance Portability and Accountability Act (HIPAA), the Gramm-Leach-Bliley Act (GLBA), or the Sarbanes-Oxley Act (SOX)—as well as state privacy regulations and European directives—without burdening the senders, recipients, or email administrators. Offer encryption not as a mandate but as a service that’s easy to use and gives the sender complete control. |
Manageability | Universal device support Make sure all users can access messages when needed, regardless of whether they are on smartphones, tablets, laptops, or desktop computers. Universal device support is designed to ensure that highly secure messages can be read by any recipient, no matter what device is used to open the message. Dedicated plug-in applications offer an enhanced user experience for Microsoft Outlook and on Apple iOS and Google Android smartphones and tablets. System overview dashboard Monitor and report on outbound messages from a centralized, custom system overview dashboard. Unified business reporting offers a single view for comprehensive insight across your organization. Get the details of any report for advanced visibility. Detailed message tracking Track a message by envelope recipient, envelope sender, subject, attachments, and message events including DLP policy or IDs. When you send a message to Cisco Email Security, the message tracking database is populated within a minute or two, and you can see what happened to the messages that are crossing the system at every step of processing. |
Security Awareness | Provides flexibility and support to effectively deploy phishing simulations and awareness training, as well as measure and report results. It focuses on user behavior training to make long-term changes, and empowers the security operations team with the ability to address real-time threats. High-quality content that includes a course builder with 150+ learning modules to choose from, role-based learning, and highly interactive content with gamification to keep users engaged. Intuitive phishing simulator that provides out-of-the-box phishing scenarios that reflect real-life cyber and phishing threats, which are integrated with training for just-in-time feedback. Multilingual content and platform with support for 40+ languages (narration and text) to make security awareness programs available globally. Communications and reinforcement materials provided by large libraries of predesigned content and templates for internal campaign promotion and content reinforcement (including videos, posters, and newsletters). Consultative approach with unique offerings, including CISO coaching, managed services, and content customization, to help organizations develop and optimize a security awareness strategy. |
Cisco Email Security Software Licenses
There are three email security software bundles: Cisco Email Security Inbound Essentials, Cisco Email Security Outbound Essentials, and Cisco Email Security Premium; add-on standalone options are also available (see Table 2). Just purchase the appropriate licenses for the number of mailboxes you need to support. For cloud and virtual appliances, simply order the software licenses to get entitlement.
Term-based Subscription Licenses
Licenses are term-based subscriptions of 1, 3, or 5 years.
Quantity-based Subscription Licenses
The Cisco Email Security portfolio uses tiered pricing based on the number of mailboxes. Sales and partner representatives will help you determine the correct customer deployment.
The major components of each software offering are provided in Table 2.
Table 2. Software components
Bundles | Description |
Cisco Email Security Inbound Essentials | The Cisco Email Security Inbound Essentials bundle delivers protection against email-based threats and includes antispam, graymail detection, Sophos antivirus solution, outbreak filters, and forged email detection. |
Office 365 Cisco Email Security Inbound Essentials | The Cisco Email Security Inbound Essentials bundle delivers protection against email-based threats and includes antispam, graymail detection, outbreak filters, and forged email detection. |
Cisco Email Security Inbound Essentials plus Cisco Advanced Malware Protection and Cisco Threat Grid | The Cisco Email Security Inbound Essentials bundle delivers protection against email-based threats and includes antispam, graymail detection, Sophos antivirus solution, outbreak filters, and forged email detection. AMP can be purchased along with any Cisco Email Security software bundle. Threat Grid and AMP augments the malware detection and blocking capabilities already offered in Cisco Email Security with file reputation scoring and blocking, sandboxing, and file retrospection for continuous analysis of threats, even after they have traversed the email gateway. AMP and Threat Grid can now be deployed completely on-premises with Cisco AMP Private Cloud Virtual Appliance. This is important for customers who have stringent policy requirements that do not allow for use of the AMP public cloud. |
Cisco Email Security Outbound Essentials | The Cisco Email Security Outbound Essentials bundle guards against data loss with DLP compliance and email encryption. |
Cisco Email Security Premium | The Cisco Email Security Premium bundle combines the inbound and outbound protections included in the Cisco Email Security Inbound and Outbound Essentials licenses noted above for protection against email-based threats and essential DLP and encryption. |
Office 365 Cisco Email Security Premium | The Cisco Email Security Premium bundle combines the inbound and outbound protections included in the Office 365 Cisco Email Security Inbound and Cisco Email Security Outbound Essentials licenses noted above for protection against email-based threats and essential DLP and encryption. |
Cisco Email Security Premium plus Cisco Advanced Malware Protection and Cisco Threat Grid | The Cisco Email Security Premium bundle combines the inbound and outbound protections included in the Cisco Email Security Inbound and Outbound Essentials licenses noted above for protection against email-based threats and essential DLP and encryption. AMP can be purchased along with any Cisco Email Security software bundle. Threat Grid and AMP augments the malware detection and blocking capabilities already offered in Cisco Email Security with file reputation scoring and blocking, sandboxing, and file retrospection for continuous analysis of threats, even after they have traversed the email gateway. AMP and Threat Grid can now be deployed completely on-premises with Cisco AMP Private Cloud Virtual Appliance. This is important for customers who have stringent policy requirements that do not allow for use of the AMP public cloud. |
Standalone Offerings | Description |
Cisco Advanced Malware Protection and Cisco Threat Grid | AMP can be purchased along with any Cisco Email Security software bundle. Threat Grid and AMP augments the malware detection and blocking capabilities already offered in Cisco Email Security with file reputation scoring and blocking, sandboxing, and file retrospection for continuous analysis of threats, even after they have traversed the email gateway. AMP and Threat Grid can now be deployed completely on-premises with Cisco AMP Private Cloud Virtual Appliance. This is important for customers who have stringent policy requirements that do not allow for use of the AMP public cloud. |
Intelligent Multi-Scan | Intelligent Multi-Scan (IMS) is a high performant multi-layer anti-spam solution that uses a combination of anti-spam engines, including Cisco Anti-Spam, to increase spam catch rates. You cannot configure the order of the scanning engines used in Cisco Intelligent Multi-Scan; Cisco Anti-Spam will always be the last to scan a message and Cisco Intelligent Multi-Scan will not skip it if a third-party engine determines that a message is spam. Using Cisco Intelligent Multi-Scan can lead to reduced system throughput. Please contact your Cisco support representative for more information. To use the updated IMS engine, you must add the IMS feature key and accept the license in your appliance. For the existing IMS users, all the mail policies for IMS are migrated to work seamlessly with the updated IMS engine. |
Graymail safe-unsubscribe | Graymail now can be tagged with a truly safe unsubscribe option. This tag manages a highly secure unsubscribe action on behalf of the end user. It also monitors the different graymail unsubscribe requests. All these can be managed at a policy, Lightweight Directory Access Protocol (LDAP) group level. |
Cisco Advanced Phishing Protection | CAPP can be purchased along with any Cisco Email Security software bundles. CAPP stops identity deception–based attacks such as social engineering, imposters, and BEC. It provides local email intelligence and advanced machine learning techniques to model trusted email behavior on the Internet, within organizations and between individuals. CAPP also integrates machine learning techniques to drive daily model updates, maintaining a real-time understanding of email behavior to stop identity deception. Offered only for one and three year subscriptions. |
Cisco Domain Protection | CDP can be purchased along with any Cisco Email Security software bundle. CDP for external email helps prevent phishing emails from being sent using a customer domain(s). The CDP service automates the process of implementing the email authentication standard DMARC to better protect employees, customers, and suppliers from phishing attacks using a customer domain(s). This protects the customers’ brand identity as well as increases email marketing effectiveness by reducing phishing messages from reaching inboxes. Offered only for one and three year subscriptions. |
Image Analyzer | Detects illicit content in incoming and outgoing email, allowing customers to identify, monitor, and educate offending users. |
McAfee AntiVirus | Offers McAfee antivirus scanning technology. |
Cisco Security Awareness | Cisco Security Awareness can be purchased along with any Cisco Email Security software bundles. It is designed to help promote and apply effective cybersecurity common sense by modifying end-user behavior and empower employees to work smarter and safer. This cloud-delivered subscription provides comprehensive simulation, training, and reporting so employee progress can be continually monitored and tracked. It helps organizations remain safe with engaging and relevant computer-based content with various simulated attack methods, and empowers the people in your organization to play a critical role in its overall security with Cisco Security Awareness. |
Software License Agreements
The Cisco End-User License Agreement is provided with each software license purchase.
Software subscription support
All email security licenses include software subscription support that is essential to keeping business-critical applications available, highly secure, and operating at peak performance. This support entitles you to the services listed below for the full term of the purchased software subscription.
● Software updates and major upgrades keep applications performing at their best, with the most current features.
● The Cisco Technical Assistance Center provides fast, specialized support.
● Online tools build and expand in-house expertise and boost business agility.
● Collaborative learning provides additional knowledge and training opportunities.
Where to deploy
All Cisco Email Security deployments options share a simple approach to implementation. The system setup wizard can handle even complex environments and will have you up and protected in just minutes, making you safer faster. Licensing is user based, not device based, so you can apply it per user instead of per device to provide inbound as well as outbound email gateway protection at no additional cost.
Cloud
Cisco Email Security in the cloud provides you with a flexible deployment model for email security. It helps you reduce costs with co-management and no onsite email security infrastructure. Dedicated email security deployments in multiple resilient Cisco data centers provide the highest levels of service availability and data protection. Customers retain access to (and visibility of) the cloud infrastructure, and comprehensive reporting and message tracking helps assure administrative flexibility. This service is all inclusive, with software, computing power, and support bundled for simplicity.
Virtual
The Cisco Email Security Virtual Appliance significantly lowers the cost of deploying email security, especially in highly distributed networks. This appliance lets your network manager create instances where and when they are needed, using your existing network infrastructure. A software version of the physical appliance runs on top of a VMware ESXi hypervisor and Cisco Unified Computing System™ (Cisco UCS®) servers. You receive an unlimited license for the virtual appliance with the purchase of any Cisco Email Security software bundle.
With the virtual appliance, you can respond instantly to increasing traffic growth with simplified capacity planning. You don’t need to buy and ship appliances, so you can support new business opportunities without adding complexity to a data center or having to hire additional staff.
On-premises
The Cisco Email Security Appliance is a gateway typically deployed in a network edge outside the firewall (the so-called demilitarized zone). Incoming SMTP traffic is directed to the appliance’s data interface according to specifications set by your mail exchange records. The appliance filters it and redelivers it to your network mail server. Your mail server also directs outgoing mail to the data interface, where it is filtered according to outgoing policies and then delivered to external destinations.
Hybrid
The hybrid solution provides you with maximum flexibility. You can mix any deployment options to best suit your needs. For example, you can take advantage of Cisco Email Security in the cloud to protect against threats in incoming messages while deploying outbound control of sensitive messages onsite. You can also choose to deploy inbound threat protection on-premises and in the cloud to transition to the cloud at your own pace.
You can also run on-premises and virtual Cisco Email Security in the same deployment. So your small branch offices or remote locations can have the same protection you get at headquarters without the need to install and support hardware at those locations. You can easily manage custom deployments with the Cisco Content Security Management Appliance or Cisco Content Security Management Virtual Appliance.
Cisco Email Security specifications
Table 3 presents the performance specifications for Cisco Email Security while Table 4 presents the hardware specifications and Table 5 presents the specifications for a virtual deployment. Table 6 presents specifications for the Secure Management Appliance M-Series Platform. Table 7 includes information on the virtual machine hardware requirements for the Cisco Advanced Phishing Protection on-premises sensor deployment.
Table 3. Cisco Email Security performance specifications
| Model | Disk Space | Raid Mirroring | Memory | CPUs |
Large enterprise | ESA C695 | 4.8 TB (600 x 8) | Yes (RAID 10) | 32 GB DDR4 | 1 x 2.6 GHz, 12 core |
Large enterprise | ESA C690 | 2.4 TB (600 x 4) | Yes (RAID 10) | 32 GB DDR4 | 2 x 2.4 GHz, 12 core |
Medium-sized enterprise | ESA C395 | 1.2 TB (600 x 2) | Yes (RAID 1) | 16 GB DDR4 | 1 x 2.1 GHz, 12 core |
Medium-sized enterprise | ESA C390 | 1.2 TB (600 x 2) | Yes (RAID 1) | 16 GB DDR4 | 1 x 2.4 GHz, 6 core |
Small to midsize businesses or branch offices | ESA C195 | 1.2 TB (600 x 2) | Yes (RAID 1) | 16 GB DDR4 | 1 x 2.1 GHz, 8 core |
Small to midsize businesses or branch offices | ESA C190 | 1.2 TB (600 x 2) | Yes (RAID 1) | 8 GB DDR4 | 1 x 1.9 GHz, 6 core |
Note: For accurate sizing, verify your choice by checking the peak mail-flow rates and average message size with a Cisco content security specialist.
Table 4. Cisco Email Security Hardware specifications
Model | ESA C695 | ESA C690 | ESA C395 | ESA C390 | ESA C195 | ESA C190 |
Rack Units (RU) | 1RU | 2RU | 1RU | 1RU | 1RU | 1RU |
Dimensions including handles (H x W x D) | 1.7 x 16.89 x 29.8 in. (4.32 x 43.0 x 75.6 cm) | 3.4 in. x 19 in. x 29 in (8.6 x 48.3 x 73.7 cm) | 1.7 x 16.89 x 29.8 in. (4.32 x 43.0 x 75.6 cm) | 1.7 x 16.89 x 29.8 in. (4.32 x 43.0 x 75.6 cm) | 1.7 x 16.89 x 29.8 in. (4.32 x 43.0 x 75.6 cm) | 1.7 x 16.89 x 29.8 in. (4.32 x 43.0 x 75.6 cm) |
DC power option | No | Yes (930W) | No | No | No | No |
Remote power cycling | Yes | Yes | Yes | Yes | Yes | Yes |
DC Power Option | No | Yes (930W) | No | No | No | No |
Remote power cycling | Yes | Yes | Yes | Yes | Yes | Yes |
Redundant power supply | Yes | Yes | Yes | Yes | Yes, accessory option | Yes, accessory option |
Hot-swappable hard disk | Yes | Yes | Yes | Yes | Yes | Yes |
Power Consumption | 2626 BTU/hr | 2216.5 BTU/hr | 2626 BTU/hr | 2626 BTU/hr | 2626 BTU/hr | 2626 BTU/hr |
Power Supply | 770W | 650W | 770W | 770W | 770W | 770W |
Ethernet interfaces | 6-port 1GBASE-T copper network interface (NIC), RJ-45 | 6-port 1GBASE-T copper network interface (NIC), RJ-45 | 6-port 1GBASE-T copper network interface (NIC), RJ-45 | 6-port 1GBASE-T copper network interface (NIC), RJ-45 | 2-port 1GBASE-T copper network interface (NIC), RJ-45 | 2-port 1GBASE-T copper network interface (NIC), RJ-45 |
Speed (Mbps) | 10/100/1000, auto negotiate | 10/100/1000, auto negotiate | 10/100/1000, auto negotiate | 10/100/1000, auto negotiate | 10/100/1000, auto negotiate | 10/100/1000, auto negotiate |
Fiber option | Yes, separate SKU, 2-port 1GBASE-SX Fiber or 10GBASESR Fiber selectable upon ordering (modules included): ESA-C695F | Yes, separate SKUs, 2-port 1GBASE-SX Fiber: ESA-C690-1G 2-port 10GBASESR Fiber: ESAC690-10G | No | No | No | No |
HD Size |
Andrew Lock | .NET Escapades
In this post I show a simple way to obfuscate email addresses to make it harder for bots to scrape them from your site. It uses a similar approach as Cloudflare Scrape Shield.
It's important to note that the encoding scheme used here is incredibly weak. But that's kind of the point. It's only meant to provide rudimentary protection against automated scraping by bots. It's obfuscation, not encryption!
Background - Cloudflare Scrape Shield
I include my email address on the about page of my blog in case people want to get in touch. I've personally only ever had pleasant emails from people (though I'm well aware that's a rarity for many people in our industry). Somewhat surprisingly perhaps, I don't get a huge amount of spam because of it.
Some time ago I moved my blog from a self-hosted instance of Ghost to Netlify. At the same time, I also removed the Cloudflare caching layer, as Netlify uses its own layer of caching. One of the features of Cloudflare is Scrape Shield. This has multiple parts to it, but the one I was most interested in was email obfuscation.
Cloudflare's email obfuscation works by modifying the HTML output of your app when they serve it. If cloudflare detects an email address in an tag, for example:
It will modify this element inline, and inject a script element:
When the page is served, the email-decode.min.js script is executed, and the tag is replaced with the original. The advantage of this is that bots need to execute the JavaScript on your page in order to retrieve your email address, which raises the barrier (slightly) for bots trying to scrape the email address from your app.
To avoid causing problems, there are a bunch of places that Cloudflare won't obfuscate email addresses. See the documentation for details.
When I moved my blog from Cloudflare to Netlify, I didn't want to lose that email obfuscation, so I looked at how I could implement it myself. Luckily, it's pretty trivial to achieve, as I found from reading this excellent post. This post is very much based on that one.
So, how does the email address "encryption" work?
Decoding an obfuscated email address
First of all, while technically encryption, the scheme is so weak, you really shouldn't think of it as that. It's more just like obfuscation. That's all that's required for our intended goal, but it's important to keep in mind.
I'll start with the decoding strategy - how do you retrieve the email address from the encoded version shown previously?
The email is encoded into the portion of the modified attribute, i.e. . In the previous example, that was:
The overall strategy to decoding this is as follows:
- Remove the first 2 characters (), and convert to its hex equivalent value (). This is the key for the rest of the calculation.
- Iterate through the remainder of the characters, incrementing by two. For each pair of characters (the first pair is ):
- Convert the pair to its hex equivalent ()
- Perform a bitwise XOR of the number with the key. so
- Convert the result () to its UTF-16 equivalent ()
- Append the result to previous results
- Repeat until all characters are consumed. The final result is the original email
The XOR scheme used is one of the most basic encryption schemes possible. And on top of that, the key for the encryption is stored right along-side the cipher text! Again, this is not secure encryption; it is simply obfuscation.
This is actually a simplified description of the cloudflare approach - Cloudflare have an additional step to handle Unicode codepoints (which can be multiple bytes long). See this blog post for a description of that step.
So how can you implement this algorithm for your own apps?
Implementing email obfuscation on your own blog
Cloudflare dynamically replaces email addresses in your HTML, and injects additional scripts into the DOM. That's not really necessary in my case - my blog is statically generated, and even if it wasn't, there's probably only a few email addresses I would want to be encoding.
Because of those constraints, I opted to encode the email address on my blog ahead of time, rather than trying to do it on-the-fly. I can also then just include the email decoding script in the standard JavaScript bundle for the site.
Encoding the email address
Given you have an email address you want to obfuscate on your site, e.g. `[email protected]`, how can you encode that in the required format?
I wrote a small JavaScript function that takes an email address, and a key in the range and outputs an obfuscated email address. It uses the algorithm from the previous section in reverse to generate the output:
I only have a couple of emails on my blog I want to obfuscate, so I ran them through this function, choosing an arbitrary key. I used Chrome's dev tools to run it - open up any old website, hit F12 to view the console, and copy-paste the function above. Then run the function using your email, picking a random number between 0-255:
The hex encoded output is what we'll use in our website.
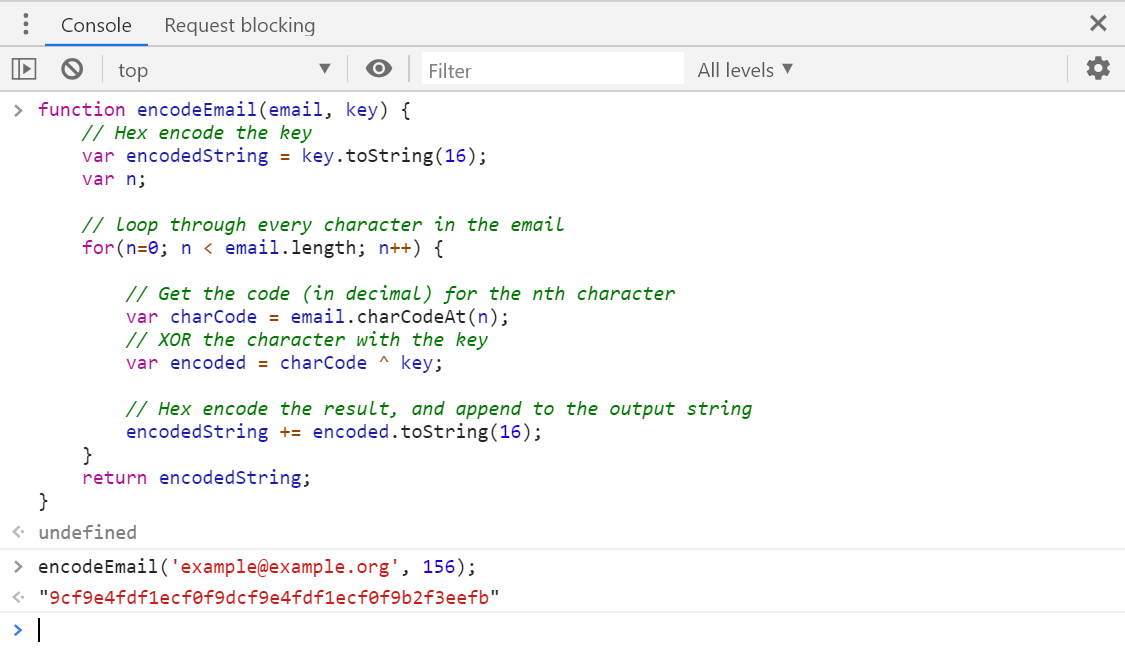
The code to decode the email is is very similar.
Decoding the email address
The function to decode an email address from the encoded string is shown below, and follows the algorithm shown previously:
When you pass this function an encoded email, you'll get your original back:
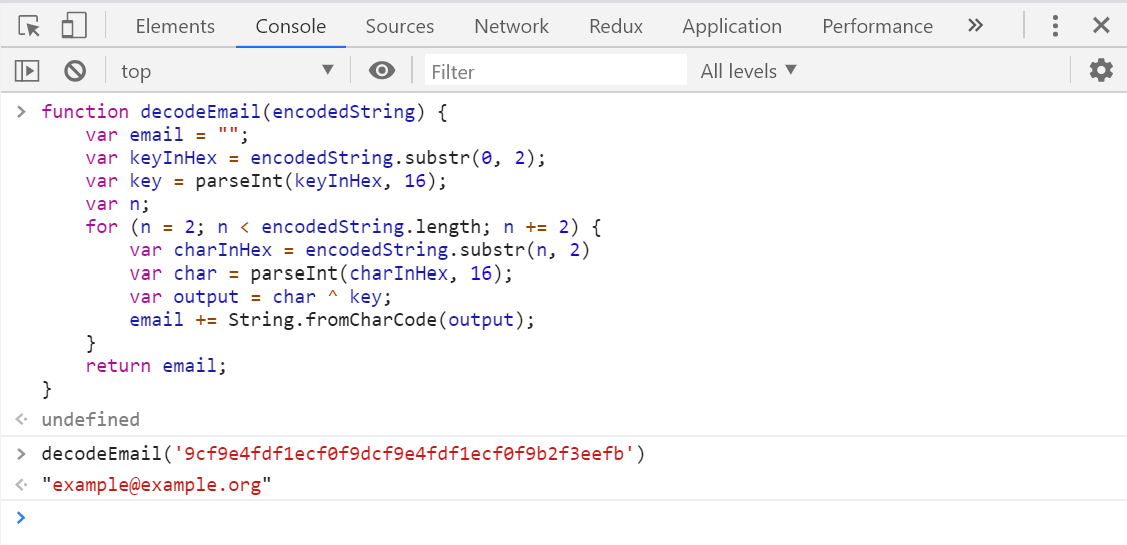
Now lets look at how to use these functions in a website.
Replacing existing emails with obfuscated emails
I only use my email in anchor tags, so I want the final (unencoded) tag on my blog to look something like the following:
In my source code, instead of the above, I use the following:
If bots scrape the website, they won't see an easily recognisable email, which will hopefully go some way to prevent it being scraped.
There's lots of different points at which you could decode the string, depending on the experience you want. You could keep the string encoded on your website until someone clicks a "reveal" button for example. I had a very simple use case, so I chose to automatically decode the email immediately when the page loads.
Hopefully the code is self explanatory, but I'll walk through it here
- Find all elements on the page with the class
- For each element:
- Fetch the inner text () in the example above
- Run the inner text through the decoder, to get the real email address
- Replace the text of the anchor to be `[email protected]`
- Set the of the anchor to be .
The code is functionally complete, but there's a lot of short-cuts:
- No error checking or handling
- Assumes that all elements are tags
- Assumes the document is fully loaded before the script runs
- Assumes the encoded email isn't corrupted or invalid
If you're applying this approach to a larger site, you don't have strict control over the contents, or any of these assumptions don't hold, then you'll probably need to be more careful. For my purposes, this is more than enough 🙂
Summary
In this post I showed how you can obfuscate email addresses on a website to make it harder for bots to easily scrape them. The encoding scheme is based on the one used in Cloudflare's scrape shield product, which uses a simple XOR scheme to hide the data as a hex-string. This is not at all "secure", especially as the key for decoding is included in the string, but it serves its purposes of obfuscating emails from automated systems.
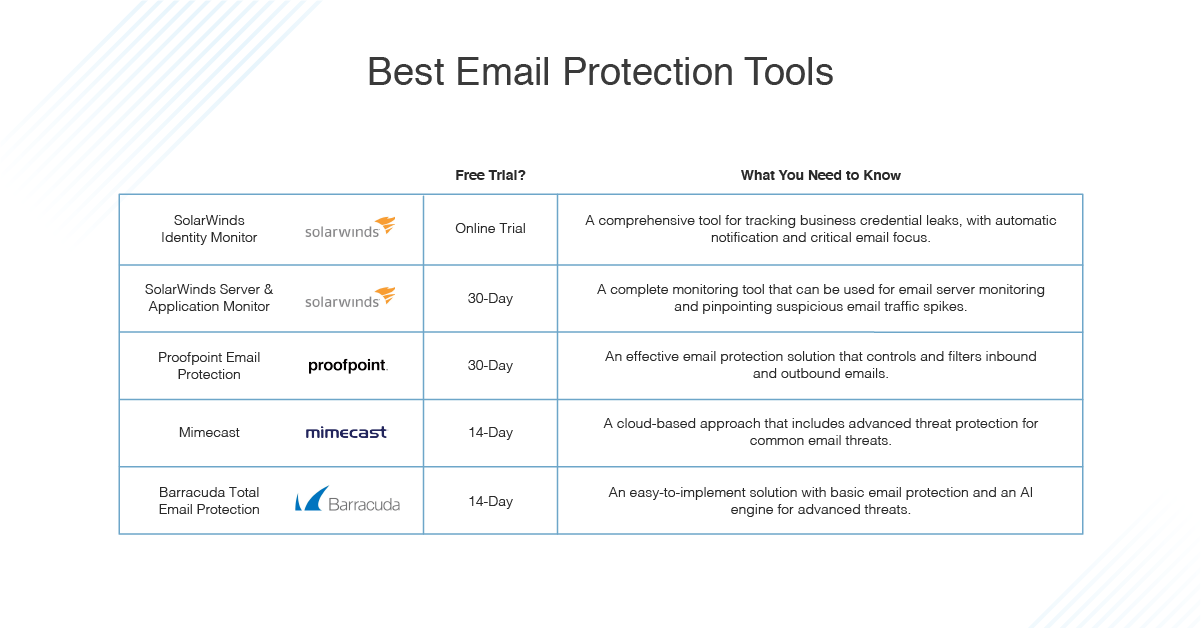
5 Best Email Protection Tools in 2020
Email protection isn’t something to be taken lightly. Email can put users at risk of scams, malware, phishing, stolen devices, and stolen passwords. Without effective email protection tools, you could be giving hackers a direct route into your data and resources.
But finding the best email protection software isn’t easy. The IT security software market has become increasingly saturated, with every email protection program claiming to be the best. I’ve created this list of the best available email protection software to help you choose between the biggest players in email data protection.
Feel free to jump ahead to each tool review:
- SolarWinds Identity Monitor
- SolarWinds Server & Application Monitor
- Proofpoint Email Protection
- Mimecast
- Barracuda Total Email Protection
In ranking these products, I’ve considered user-friendliness, range of functionality, sophistication of features, and the trustworthiness of the vendor. Overall, SolarWinds® Identity Monitor ranks the highest. This email protection program balances range, ease of use, and sophistication. To find out more about Identity Monitor and how the other products compare, check out my list below.
- SolarWinds Identity Monitor
SolarWinds Identity Monitor is a comprehensive and dynamic email protection program. It’s first on this list because its features combine scope, genuine usefulness, and sophistication to deliver a truly enterprise-grade email protection tool. This program employs an attractive user interface designed to be simple and easy to navigate. And unlike many tools on the market, it’s scalable and doesn’t compromise on value as your company grows.
Identity Monitor offers three main capabilities to prevent account takeover:
- Monitoring your email domains for any signs of exposure
- Notifying you of any leaked data
- Resetting passwords before they’re compromised
This tool allows you to establish a domain watch list, which is viewable in a table format. Alongside the domain name, you’ll see when the domain was last discovered, the number of corporate records associated with it, its status, and whether it’s verified. You can perform actions on each of the domains within this page, edit the number of entries you can see, adjust column visibility, and conduct searches. You can also sort information to reflect your priorities.
As soon as a leak is identified, Identity Monitor notifies you, so you can take immediate action. This might include interrogating recent logins or resetting passwords. You can also force password resets for impacted accounts. The program gives you recommendations to keep your team informed on email protection best practices, like maintaining a password manager and using unique credentials.
Identity Monitor is always analyzing new data leaks, alerting you to how many of your corporate records have been discovered in a breach and how sensitive the source is. All collected data is accompanied by contextual details revealing the severity of the breach and the primary concern associated with it (e.g., password reuse).
This email data protection tool lets you add IPv4 CIDR or IPv4 addresses to your watch list, monitoring them for breaches and botnets. You can also monitor the private email credentials of key employees as well as multiple domains.
You can try Identity Monitor for free by entering your credentials into the site, which will show your current level of exposure. A free trial is also available.
- SolarWinds Server & Application Monitor
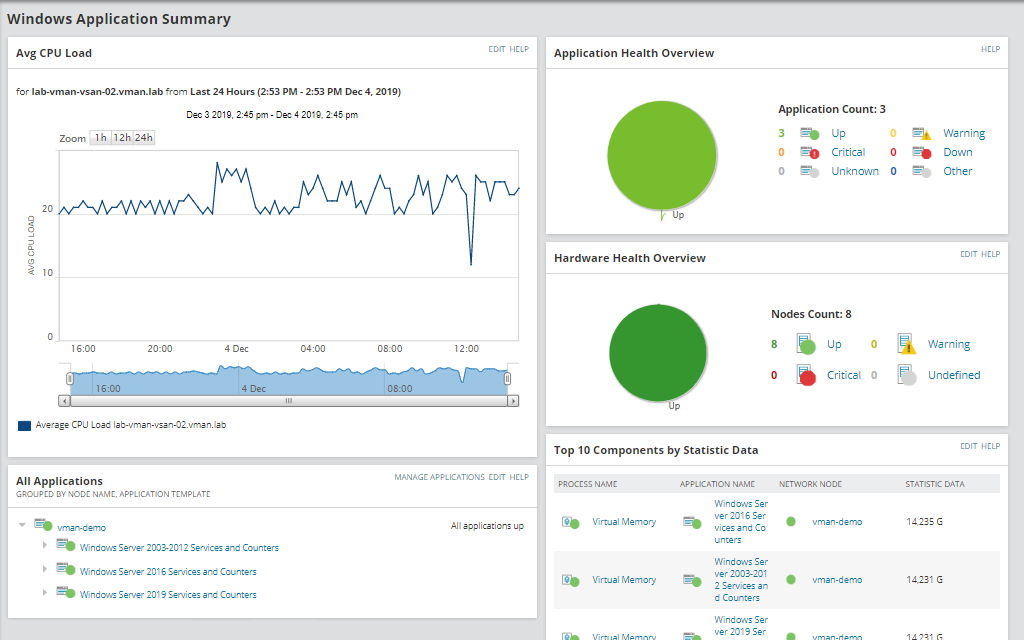
SolarWinds Server & Application Monitor (SAM) isn’t strictly a security solution. It’s an email monitoring tool and an essential part of wider monitoring processes.It’s also highly effective because it consolidates all your email monitoring into a single dashboard. This streamlines your email security and oversight, so you’re always informed.
SAM comes with out-of-the-box mail Exchange server monitoring capabilities, giving you detailed insight into patterns of behavior possibly resulting in poor performance. This includes testing round-trip time and email delivery success for MAPI, POP3, and IMAP4 mail protocols. You can monitor email servers from the end user’s perspective and gain visibility across all top web email clients, including Microsoft Outlook Web Access. This program is powerful enough to manage high email rates, POP3 requests, and MAPI operations, so it can meet the requirements of growing enterprises.
SAM identifies CPU bottlenecks in email servers and unusual spikes in email traffic. It’s able to diagnose issues related to storage, replication, database capacity, and RPC requests in a matter of minutes, and it can troubleshoot in real time. Troubleshooting is supported by historical performance-related data. You can use SAM to view the size of a database, the amount of space currently in use, the total number of mailboxes, and the average size of a mailbox.
SAM is a great tool for investigating potential email issues. It enables you to drill down into key information, search for users, and troubleshoot user problems in Exchange. You can view the size and number of mailbox attachments, patterns in sent and received emails, and synchronized devices, which can assist with the identification of spam issues associated with a user’s account.
Because email protection cannot be achieved without effective email monitoring capabilities, SAM is a valuable addition to any IT monitoring solution. The level of insight this tool provides is unrivaled, affording you rare visibility into your email servers capable of directly informing the actions you take to protect them. You can try a fully functional free trial of SAM for 30 days.
- Proofpoint Email Protection
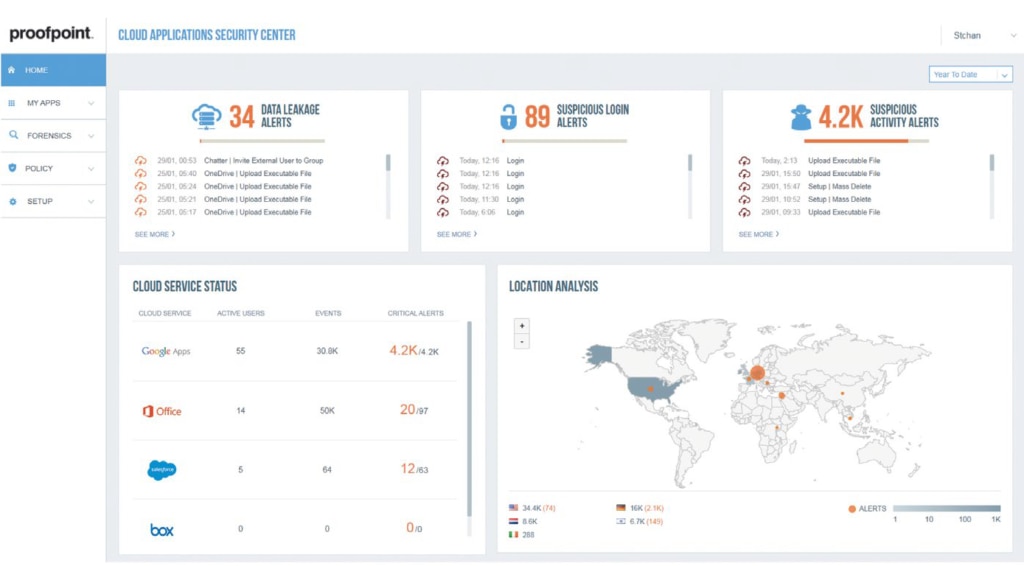
Proofpoint provides many IT security products, including Advanced Threat Protection, Security Awareness Training, Cloud App Security, Information Protection, and Digital Risk Protection. As a security-focused vendor, it’s no surprise the company’s email protection solution is effective. Proofpoint Email Protection establishes numerous security layers to make it as difficult as possible for malware and non-malware threats to infiltrate your email.
This program controls every component of outbound and inbound email, identifying and blocking threats before they deal damage. It also prevents private information from being compromised, shared, or accessed by the wrong people. Email Protection lets you establish email filtering policies as well as complex firewall rules and antivirus policies.
Email Protection leverages everything at its disposal, including user bulk mail actions, to improve future detection accuracy. The program uses a Stateful Composite Scoring Service (SCSS)—a machine learning operation—to recognize and prevent impostor attacks. SCSS learns from your environment and uses Proofpoint customer data to continuously improve its email fraud blocking capacity.
However, Proofpoint Email Protection isn’t as user-friendly as it could be, and it has a steep initial learning curve. You can watch a demo here.
- Mimecast
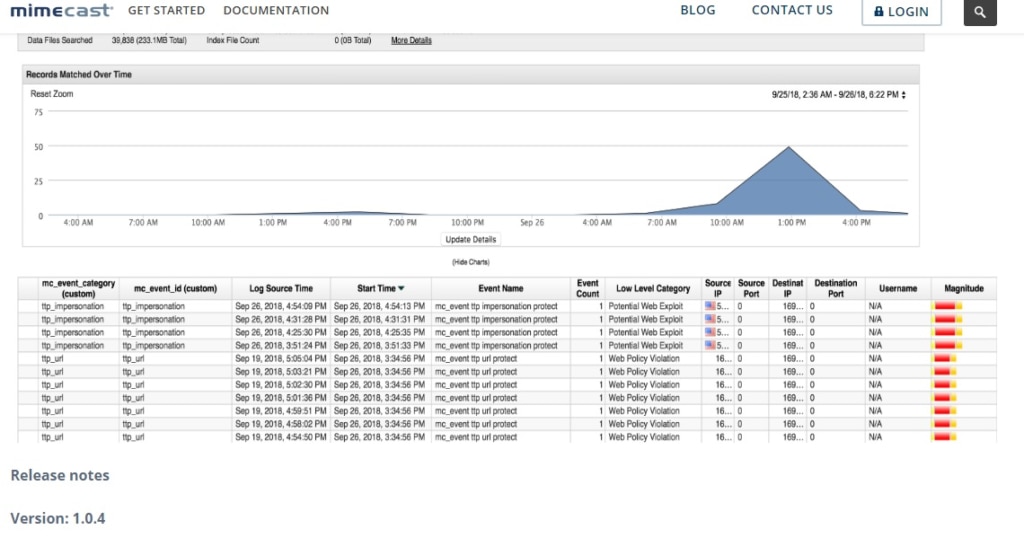
Mimecast offers a cloud-based approach to email protection software. Cloud-based programs can be accessed from anywhere, provided you have an internet connection. The Mimecast solution is intelligent and continuously evolving to keep pace with increasingly insidious and sophisticated threats.
Mimecast is a comprehensive program providing advanced threat protection against spear phishing, email compromise attacks, malicious URLs, weaponized attachments, fraud, social engineering, and much more. It also offers data leak protection, secure messaging, and secure transfer for large files.
There’s zero capital outlay associated with this program, and because it’s cloud-based, Mimecast lets you conveniently deploy company-wide security policies from a single web-based console. However, there is some disagreement about how secure cloud-based solutions are, and some IT administrators will prefer on-premises programs. You can schedule a demo of Mimecast.
- Barracuda Total Email Protection
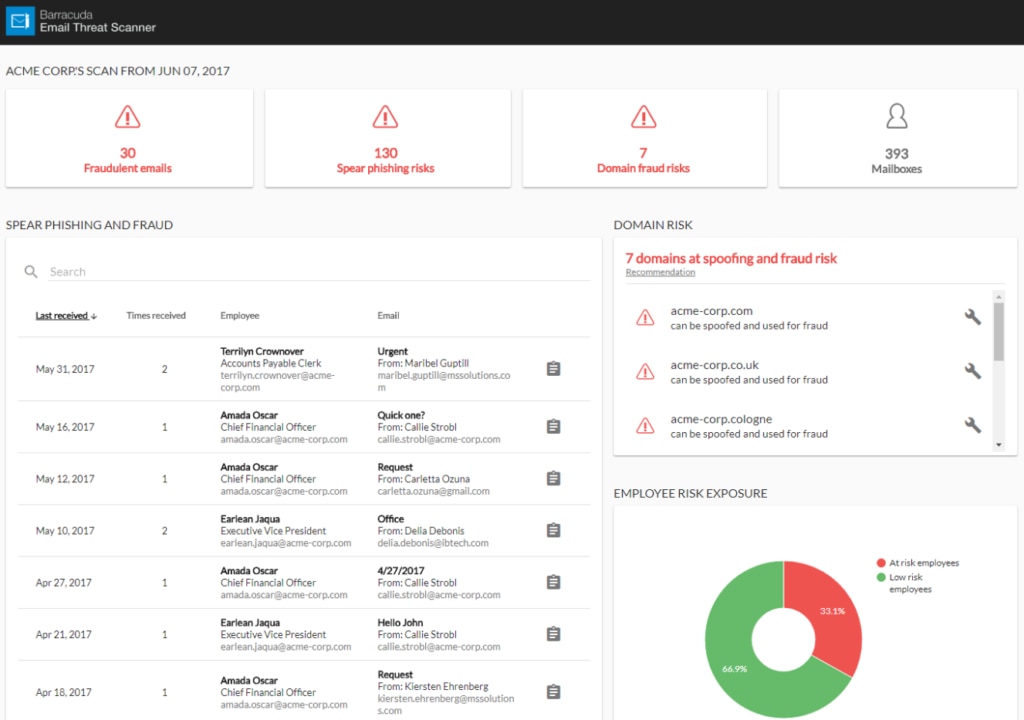
Barracuda Total Email Protection is a bundled solution combining Barracuda’s full range of email protection tools. This bundle is easy to implement and combines basic email protection utilities—like spam blocking, encryption, backup, archiving, and email filtering—with spear phishing simulations, full training, and much more. This bundle is a one-stop solution for email protection, which simplifies due diligence and post-purchase evaluation and eradicates the need to integrate with other products.
Barracuda Sentinel, one of the products included in the bundle, uses a powerful AI engine to detect advanced threats, including targeted spear phishing attacks and account takeover. Barracuda PhishLine, another included product, offers email protection training in the form of a spear phishing simulation platform. With this tool, you can learn to identify email threats, even on devices outside corporate email gateways. Lastly, Barracuda Forensics and Incident Response automates incident response operations, proposing remediation options so you can manage attacks rapidly and effectively.
Barracuda Total Email Protection is an enterprise-grade email protection program, but it may not be suitable or cost-effective for smaller organizations. It could also be more beginner-friendly, as learning to navigate the user interface takes some time. You can request a free evaluation at the bottom of this page.
Choosing the Best Email Protection Software
SolarWinds Identity Monitor stands out as the best email protection tool. The software’s range of functionality is impressive, and its user interface is easy to navigate. This beginner-friendly program offers an enterprise-grade experience at a fair price.
A provider’s reputation is always important to consider, as many vendors provide top-quality tools but can’t be relied upon to maintain prices. SolarWinds has a consistent track record of producing some of the best enterprise-grade IT tools available. Its product range is dependable and well supported. If you’re looking for the best email protection software available, Identity Monitor is the tool for you.
What’s New in the Email Protection | Cloudflare?
Screen Shot

System Requirements for Email Protection | Cloudflare
- First, download the Email Protection | Cloudflare
-
You can download its setup from given links:


