
Malwarebytes activator Archives

malwarebytes activator Archives
Malwarebytes Premium v4.1.2.73 Download + Activation / License Patcher
Introduction
Malwarebytes Anti-Malware is an anti-malware application that can thoroughly remove even the most advanced malware. It is a very effective application especially designed to keep malware away from your computer. It includes a number of features, including a built-in protection monitor that blocks malicious processes before they even start. Malwarebytes Anti-Malware monitors every process and stops malicious processes before they even start. The Realtime Protection Module uses our advanced heuristic scanning technology that monitors your system to keep it safe and secure. In addition, we have implemented a threats center that will allow you to keep up to date with the latest malware threats.
Malwarebytes Anti-Malware is considered to be the next step in detecting and removing malware. We have compiled a number of new technologies that are designed to quickly detect, destroy, and prevent malware. Malwarebytes’ Anti-Malware can detect and remove malware that even the most well-known Anti-Virus and Anti-Malware applications on the market today cannot.
key Features
- Support for Windows 2000, XP, Vista and 7 (32-bit and 64-bit).
- Light speed quick scanning.
- Ability to perform full scans for all drives.
- Malwarebytes’ Anti-Malware Protection Module. (requires registration)
- Database updates released daily.
- Quarantine to keep threats and restore them at your convenience.
- Ignore list for both scanner and Protection Module.
- Freeware Settings to enhance your Malwarebytes’ Anti-Malware performance.
- A small list of extra utilities to help remove malware manually.
- Multi-lingual support.
- Works together with other anti-malware utilities.
- Command line support for quick scanning.
- Context menu integration to scan files on demand.
System Requirements
- Windows 10, Windows 8.1, Windows 8, Windows 7 SP1 (64-bit)
- CPU : Minimum 800 MHz with SSE2 technology
- RAM: 2 GB (64-bit OS), 1 GB (32-bit OS)
- Free disk space: at least 250 MB
- Recommended screen resolution: 1024×768 or higher
Download
Malwarebytes Premium v4.1.2.73
Keygen Patcher LicenseMalwareBytes Download
Installation Guide
Run to install the software
Open MalwareBytes, select , open , enter IP into and enter port into to .
Close MalwareBytes
Unzip and run as an administrator
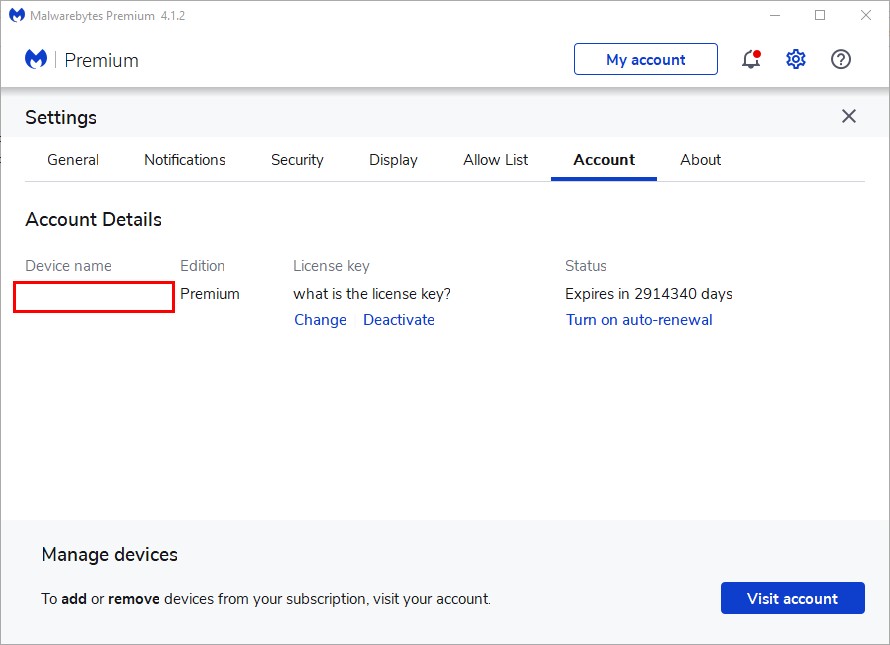
Open MalwareBytes, switch the tab , and then check if the license is available
Return to the tab and turn it off.
Switch the tab , you should have seen the premium license
Finish, enjoy~
免责声明:本站大部分下载资源收集于网络,只做学习和交流使用,版权归原作者所有,请在下载后24小时之内自觉删除,若作商业用途,请购买正版,由于未及时购买和付费发生的侵权行为,与本站无关。本站发布的内容若侵犯到您的权益,请联系站长删除,我们将及时处理! Disclaimer: Most of the download resources on this site are collected on the Internet, and are only used for learning and communication. The copyright belongs to the original author. Please consciously delete within 24 hours after downloading. If you use it for commercial purposes, please purchase the original version. If the content posted on this site violates your rights, please contact us to delete it, and we will deal with it in time!
联系我们 Contact us
觉得文章有用就打赏一下文章作者
支付宝扫一扫打赏

微信扫一扫打赏

LiliMisc: 64-bit: Restored correct manifest (from pre6. 22) with compat records so Win 10 does not lie about version number and re-added 24-bit large PNG icon liliNew Analysis: Added support for clickable links. If you put link URL in any cell of Analysis result list it creates a clickable row. If you double click on the row while holding down ALT key it will open the link liolpstrongCHANGES FOR VERSION 6.
0strong (as compared to 6.
.What’s New in the malwarebytes activator Archives?
Screen Shot

System Requirements for Malwarebytes activator Archives
- First, download the Malwarebytes activator Archives
-
You can download its setup from given links:


