
K7 total security 2016 Archives
k7 total security 2016 Archives
VB100 Comparative Review on Windows Server 2016
John Hawes
Virus Bulletin
Copyright © 2016 Virus Bulletin
Introduction
It was an all-new platform for this month's VB100 comparative, with our first look at Microsoft's latest server‑grade operating system variant, Windows Server 2016. Although the platform was officially released only shortly before the test got under way, previews had been available for some time, and being largely similar to the widely deployed desktop equivalent Windows 10, we hoped that security developers would have had plenty of time to ensure their products supported the new environment to the full. However, any new setup will inevitably bring some surprises, so we were more than usually keen to see just how well products would perform this month.
Platform and test sets
Installation, as usual using standard install media acquired through the MSDN programme, proved fairly simple, and the preparation of our test systems, including the addition of our standard selection of common tools, went smoothly too. Trials of our test automation systems, such as our performance measurement tools, brought up nothing untoward either, with all necessary tweaks already having been made for Windows 10 testing. However, one major change in the platform was clear from the start: for the first time on a Windows Server platform, the built-in Windows Defender anti-malware solution was enabled by default. With many of our regular participants having warned us to watch out for this, alerting us to the fact that many of them had not been provided with suitable means of disabling the protection automatically, and that there had been numerous reports of disabled setups reverting unexpectedly to an enabled state, we opted to shut Defender down for ourselves and monitor its status closely throughout testing.
As is our standard approach for speed and performance measures, baselines were taken with the system in its default state, which in this case meant with Defender enabled. The aim of this approach is to enable users to judge how much of an impact each solution has on the speed of a standard system compared to a basic, unmodified installation. This time, however, we quickly noticed something of a problem – almost every product appeared to be running much faster than the baseline times, with significantly lower resource usage too.
The resulting flood of negative numbers made our usual speed graphs rather difficult to read, and after some analysis and consideration we eventually decided to break from our standard practice and rebuild the baseline measures using unprotected, bare systems rather than the default setup for the chosen platform. This gave us a much more easily consumed set of speed data for this report. To give some indication of how Windows Defender fits into the picture, we've included for reference in the main performance and on-access lag time charts the performance numbers that were originally intended to be baselines, although as Defender was not officially submitted for testing, no full set of detection data is available.
The test deadline was set for 2 November, a little later than usual due to the VB conference having taken up a lot of our time in October. Our sample sets were frozen on 2 November and we used the latest WildList available at the time, v4.033. As always, our clean sets were updated and tidied in preparation for the test, with the latest version comprising around 850,000 files and 180GB of data.
With all preparations complete, we settled down to find out how the products would fare on the new platform.
Results
AhnLab V3Net for Windows Server
Main version: 9.0.22.7 build 919
Update versions: 2016.11.02.01, 2016.06.25.00, 2016.11.23.05, 2016.11.29.04
Last 6 tests: 1 passed, 0 failed, 5 no entry
Last 12 tests: 3 passed, 0 failed, 9 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 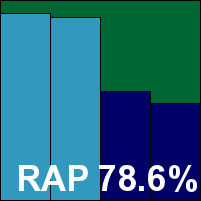 |
AhnLab's products tend to pop up in our tests at fairly random intervals, but generally put in decent performances. The latest server edition looks slick and glossy with a clean and clear layout, and proved to run pretty smoothly on Windows Server 2016 with only a single incident of the product GUI crashing out. Our performance measures showed pretty low use of resources and a fairly sizeable slowdown of our set of standard tasks, although they still ran through a good bit faster than with Windows Defender operational. File read times were also a little slow on first encounter of items, but again mostly better than with Defender enabled, and they sped up considerably on repeat runs. Scanning speeds looked decent too, particularly over the local system partition.
Detection was strong in the response sets, dropping off fairly considerably in the offline reactive sets. The core certification sets were handled nicely though, and AhnLab kicks off this month's test with a VB100 award.
Avast Business Security
Main version: 12.3.2515 build 12.3.3154.0
Update versions: 161102-0, build 12.3.3154.23/161116-0, 161122-0, 161128-0
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 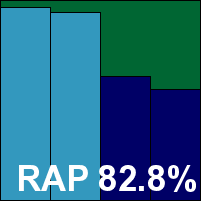 |
Avast is a much more regular participant in our tests, with a 100% pass rate in recent years. The vendor's business edition has a slick and attractive appearance that is similar to that of its home‑user offerings, with simplicity on the surface and a wealth of configuration options available. The product demonstrated good stability for the most part – the only issue noted occurred at the end of the offline RAP test, when the entire machine froze and required a reboot. This was not reproducible however, and occurred at a time of high stress, so didn't dent the stability rating too heavily.
Speeds were not the fastest on demand, but on-access lag times were light, especially in the warm runs. RAM usage was low, CPU use a little high, and our set of tasks ran through a touch slowly. Detection was strong in the response sets, tailing off somewhat in the offline part of the sets. The certification sets presented no difficulties though, and Avast maintains its clean run of passes.
Avira Antivirus Server
Main version: 15.0.23.58
Update versions: 8.12.131.62, 8.12.134.48, 8.12.136.252, 8.12.138.86
Last 6 tests: 3 passed, 1 failed, 2 no entry
Last 12 tests: 7 passed, 1 failed, 4 no entry
ItW on demand: 100.00%
ItW on access: 99.68%
False positives: 0
Stability: Solid
 | 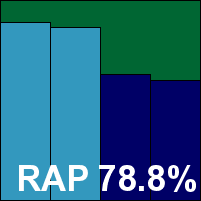 |
Avira's products show up in most of our tests and generally put in strong performances. The server version has the usual simple, angular appearance with a strong set of controls under the covers, and this month held up well under the pressure of testing with no stability problems noted. Scanning speeds were decent, while file read times look fast thanks to there being limited scanning on-read by default. Performance measures show slightly elevated resource usage and a noticeable but not too heavy impact on our set of activities.
Detection was decent too, and there were no issues in the clean sets. There was a clean run over the WildList sets on demand, but on access we noted a couple of items that were not being alerted on; further checking revealed a detection was being prevented by the cloud lookup system, a problem Avira picked up on rapidly and fixed without intervention from us. Nevertheless, it was enough to deny Avira a VB100 award this month, despite another good showing.
Bitdefender Endpoint Security
Main version: 6.2.10.832
Update versions: 7.67876, 7.68036, 7.68137, 7.68262
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 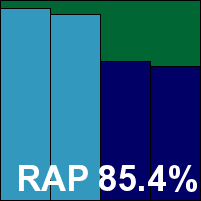 |
One of the very few vendors maintaining a perfect score card over the last two years, Bitdefender's business product has a minimalist appearance, with large fonts and clear messaging making up for minimal controls (most of which are provided in a separate management system). Stability was for the most part very good indeed, although during one large scan job we did note the PC freezing up and needing a restart, an incident which was not repeated and only occurred during unusually heavy usage.
Scanning speeds were pretty decent to start with and blasted through in no time on repeat runs, while file read lags were low and resource consumption also nominal, with a low impact on our set of activities. Detection was very strong indeed, dropping off a little into the proactive sets, and with a flawless run through the certification sets another VB100 award is well earned by Bitdefender.
CYREN Command Anti-Malware
Main version: 5.1.38
Update versions: 5.4.25/201611021006, 201611171229, 201611230923, 201611282121
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 6 passed, 4 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 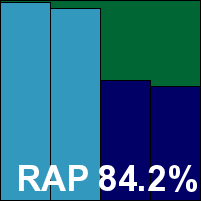 |
CYREN's venerable Command product has picked up a good string of passes of late, its earlier, long-running issues with false positives seemingly now in the past, although the product remains the unchallenged title holder in the 'most retro interface' category. Stability was reasonable in everyday use, although scanning unusually large sets of malware seemed like a fairly sure-fire way to crash the GUI. Scanning speeds were sluggish, file read lags pretty hefty, and our set of activities took a long time to complete, with low resource usage figures more a reflection of the long period over which the numbers were averaged out rather than any particular efficiency.
Detection was very strong in the reactive sets, distinctly lower in the proactive tests where the product had no access to cloud lookups, and the WildList was nicely covered. The clean sets were once again handled without issues, and another VB100 award goes to CYREN.
Defenx Security Suite
Main version: 15.0.0106
Update versions: 9.244.21362, 15.1.0103/9.245.21537, 9.245.21583, 9.245.21644
Last 6 tests: 1 passed, 0 failed, 5 no entry
Last 12 tests: 6 passed, 0 failed, 6 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 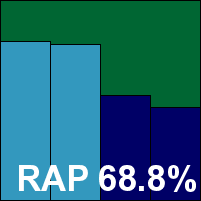 |
Defenx seems to be back in our regular lineup after a brief absence, having replaced its previous technology provider with K7. The product interface is clean and clear with good controls and plenty of information available, and seemed to brush off any attempt to stress it, earning top marks for stability. Scanning speeds were decent with some good optimization in the warm runs, while file read times weren't slowed down too much and our set of tasks completed in good time too, with minimal resource usage.
Detection was a little lower than most this month, but within acceptable bounds, and with another clean run over the certification sets a VB100 award is easily won by Defenx.
eScan Internet Security Suite Server Edition
Main version: 14.0.1400.1948 DB
Update versions: N/A
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 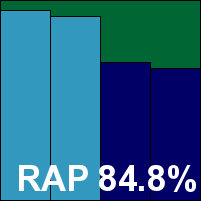 |
Another member of the 12/12 club with a perfect pass record in recent years, eScan's server edition has a very bright and colourful tiled main screen, with other areas including the ample set of configuration options looking a little less slick, but generally working well. We noted a single GUI crash, during normal usage, as well as a single problem with logging not behaving as expected, but nothing too serious. Scanning speeds were impressive, file access lags pretty light for the most part, and our set of activities wasn't hit too hard, with reasonable resource consumption.
Detection, assisted by the Bitdefender engine, was strong with a slight drop into the proactive sets, and a good showing in the core sets earns eScan another VB100 award.
ESET Endpoint Antivirus
Main version: 6.4.2014.0
Update versions: 14376, 14453, 14485, 14517
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 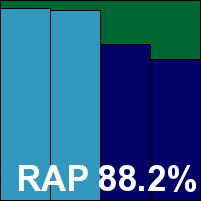 |
Fresh from celebrating an epic 100th VB100 pass, ESET returns this month to extend that splendid record of passes still further. The product is highly polished and professional-looking with plenty of data displayed and easy access to a comprehensive set of configuration options. Stability was impeccable once again with no wobbles even under seriously heavy loads, and speeds were good too, with fast scan times, light slowdown of file reads and a pretty reasonable impact on our sets of activities; resource use wasn't excessive either.
Detection was excellent with good scores even into the offline proactive sets, and yet another perfect run through the certification sets easily earns ESET its 101st VB100 award.
ESTsoft ALYac
Main version: 3.0.1.3
Update versions: 16.7.12.1/606898.2016110222/7.67876/7724183.20161102, N/A 16.7.12.1/611979.2016112322/7.68135/7323290.20161123, 16.7.12.1/613740.2016113019/7.68254/7398571.20161130
Last 6 tests: 4 passed, 1 failed, 1 no entry
Last 12 tests: 9 passed, 1 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 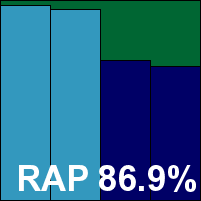 |
ESTsoft has a pretty decent record in our tests, with some good runs of passes over the last few years. The current product is pleasant to look at overall, with decent controls available, although fonts look a little wonky in places. Stability was good, with only a single issue noted, related to log exporting. Scanning speeds were fairly fast, file read lag times mostly very low, although executables were held up rather longer than other file types, at least on first visit, with warm times much better. Our set of tasks was slowed down a little but not too much, with resource consumption barely detectable.
Using the Bitdefender engine, detection was, as expected, very solid indeed, and with no problems in the certification sets another VB100 award is comfortably earned by ESTsoft.
Fortinet FortiClient
Main version: 5.4.1.0840
Update versions: 5.00233/40.00475, 40.00789, 40.00945, 41.00070
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 10 passed, 0 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair
 | 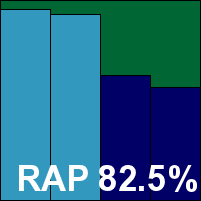 |
Fortinet's FortiClient is another extremely reliable participant in out tests, with passes in all Windows comparatives in the last few years. The product interface is fairly basic with minimal options provided and styling pared down for maximum simplicity. It proved mostly reliable, although a few update attempts failed and had to be re-run and we did see a couple of unexpected restarts. Scanning speeds were fairly slow, on-access lags a little high but showing some improvement on repeat visits to the same files, and our set of tasks was somewhat slowed down with resource consumption a little elevated at busy times.
Detection was very strong in the response sets, dropping considerably into the offline proactive sets, and the core certification sets were dealt with very tidily, earning Fortinet another VB100 award.
G DATA Antivirus Business
Main version: 14.0.1.122
Update versions: AVA 25.8921/GD 25.8081, AVA 25.9066/GD 25.8184, AVA 25.9174/GD 25.8237, AVA 25.9311/GD 25.8290
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 10 passed, 0 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 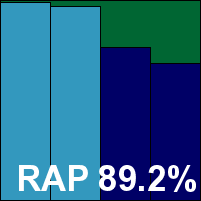 |
G DATA's business solution is a proper corporate offering with an MMC console to provide deployment and central control, and a local agent with limited configuration to keep the user informed of any issues. As usual, deployment and operation proved a little more involved than with straightforward monolithic solutions, but it seemed to work pretty well with some practice, and proved robustly resistant to the stresses of the test, earning a perfect rating for stability. Scanning speeds were reasonable initially and very fast indeed in the warm runs, with file read lags showing a similar improvement on repeat visits. Our set of activities was distinctly slower than the baseline measures, with pretty heavy use of resources too.
Detection was very strong as usual, with good scores across the sets, and another perfect showing in the core sets earns G DATA another VB100 award.
IKARUS anti.virus
Main version: 2.13.19
Update versions: 98759, 98804, 98822, 98841
Last 6 tests: 3 passed, 2 failed, 1 no entry
Last 12 tests: 7 passed, 2 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 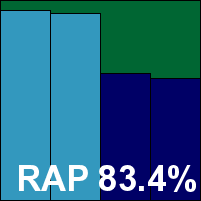 |
Ikarus seems slightly more prone to false positives than most, but has managed to pick up a decent scattering of passes of late. This month the product looked much the same as ever, the interface somewhat blocky and clunky but reasonably usable, and it proved impressively stable with no problems noted at all.
Scanning speeds started out decent and became excellent on repeat runs, while file lags were fairly significant on first seeing things but again improved impressively after initial settling in. Our set of tasks completed in very good time.
Detection was solid, with a sharpish drop into the proactive sets, and a good job handling the certification sets earns Ikarus another VB100 award.
K7 Total Security
Main version: 15.1.0330
Update versions: 9.244.21382, 9.245.21527, 9.245.21582, 9.245.21644
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 10 passed, 0 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 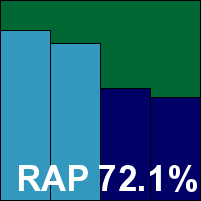 |
K7's history in our tests shows an impressive run of success of late, with passes in all Windows comparatives in the last couple of years. The product has a rugged appeal with a good set of controls within easy reach, and proved pretty stable once again with only a single glitch – a fairly minor one where an update failed to complete first time but got the job done without difficulty on re-running. Scanning speeds were slow to start with but a lot quicker on second attempt, while file read lag times were a little high, improving somewhat in the warm runs. Our set of tasks wasn't slowed down too much though, and resource usage was low.
Detection was reasonable, a little lower than the bulk of participants but still respectable, and the core certification sets were handled accurately, earning K7 a VB100 award.
Kaspersky Anti-Virus 10 for Windows Servers
Main version: 10.0.0.486
Update versions: N/A
Last 6 tests: 1 passed, 0 failed, 5 no entry
Last 12 tests: 6 passed, 0 failed, 6 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 |
Kaspersky's history in our tests is complicated somewhat by the vendor's large number of product lines, which appear in differing combinations depending on the test. The server solution is a full enterprise offering leveraging the MMC system for its main interface and controls, which are provided in the comprehensive depth one would expect and seem fairly simple to navigate and operate. There were no stability problems noted, earning the product a 'Solid' rating. Scanning speeds were not the fastest, and overheads seemed a little heavy too, with a long time taken to complete our set of tasks and fairly high use of RAM and CPU cycles.
The certification sets were nicely covered though, earning Kaspersky another VB100 award.
NANO Antivirus Pro
Main version: 1.0.46.78415 Pro
Update versions: 0.14.26.8452, 1.0.46.78415 Pro/0.14.26.8560, 1.0.70.78864 Pro /0.14.26.8596, 1.0.70.78864 Pro/0.14.26.8630
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 4 passed, 2 failed, 6 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 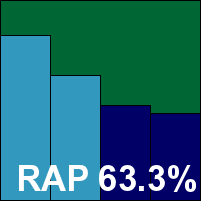 |
A relative newcomer to VB100 testing, NANO has accumulated a nice little set of passes. The product looks clean and simple, and managed to complete all tests without the slightest sign of instability. Scanning speeds were steady and not too slow, while file read lags were slow over archives but not bad elsewhere. Our set of tasks was somewhat slowed down, and resource usage was also noticeable, but not too heavy.
Detection still lags behind the leaders somewhat but continues to improve steadily, and with a good run through the certification sets, another VB100 award goes to NANO.
PC Pitstop PC Matic Home Security
Main version: 2.0.0.6
Update versions: 2.0.0.6, 2.0.0.7
Last 6 tests: 0 passed, 4 failed, 2 no entry
Last 12 tests: 0 passed, 7 failed, 5 no entry
ItW on demand: 98.95%
ItW on access: 85.72%
False positives: 2174
Stability: Buggy
 | 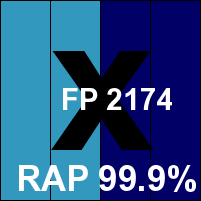 |
PC Pitstop's unusual whitelisting-heavy approach has earned it some stellar detection rates of late, although a tendency to false alarm has meant no certification for a while. The interface is focused on software vulnerabilities with some information on malware protection and basic configuration controls. The GUI itself remained reasonably stable, but we saw a number of fatal blue-screen incidents at all stages of the test (to be fair, we should note that the product is mainly geared towards the consumer market and not intended for use on server platforms). With so many issues noted no speed or performance data could be gathered, but we at least managed to complete all the detection tests, which showed once again some superb detection rates in the RAP sets, but a high FP rate and some issues with the WildList too, meaning there is no VB100 award for PC Pitstop once again.
Quick Heal AntiVirus Server Edition
Main version: 17.00 (1.0.0.4.3) 64bit
Update versions: N/A
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 8 passed, 0 failed, 4 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 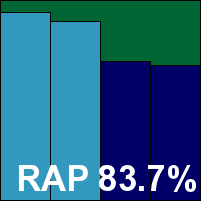 |
Quick Heal's server version has a stark black-and-white colour scheme, leavened only occasionally with touches of green or red, and a clean, pared-down layout which nevertheless manages to provide a decent set of configuration options. Stability was good, with just a single incident observed of the scanner snagging. Scanning speeds were slowish, overheads not too bad to start with and barely discernible on repeat visits, while our set of activities wasn't too badly slowed down but resource consumption was on the high side.
Detection was strong, with a steady but not too steep decline through the sets, and the certification sets were nicely dealt with, earning Quick Heal a VB100 award.
Quick Heal Seqrite Antivirus Server Edition
Main version: 17.00 (10.0.5.3) 64bit
Update versions: N/A
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 8 passed, 0 failed, 4 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 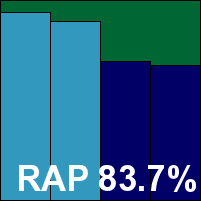 |
Quick Heal's Seqrite product line is aimed at the larger enterprise, but the main interface closely resembles other Quick Heal products, once again using a monochrome look to lend gravitas. Stability was good again, with just that single file tripping up the scanner and, this time, an update attempt returning an error on first try. Scanning speeds and file access lag times were acceptable, with a fairly large hit on our set of activities and somewhat elevated resource consumption.
Detection was pretty decent across the board, including in the certification sets where no issues were noted, duly earning Quick Heal's Seqrite another VB100 award.
Tencent PC Manager
Main version: 11.6.26315.901
Update versions: 11.6.26322.901, 12.1.26326.901, 12.1.26328.901
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 7 passed, 0 failed, 5 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 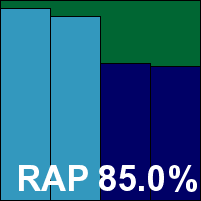 |
Chinese giant Tencent continues to build a steady run of passes in our tests. The latest edition looks bright and glossy with clear controls and a decent set of configuration options provided. Stability was dented only by an incident on one install where the on-access protection seemed to take rather a long time to kick in. Scanning speeds were on the slow side, and with minimal protection on-read our file access measures show low impact. Detection was strong, and with another good run through the certification sets, Tencent picks up another VB100 award.
Tencent PC Manager – TAV
Main version: 11.6.26311.901
Update versions: 11.6.26321.901, 12.1.26325.901, 12.1.26327.901
Last 6 tests: 3 passed, 0 failed, 3 no entry
Last 12 tests: 3 passed, 0 failed, 9 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid

The 'TAV' edition of Tencent's PC Manager uses only in-house technology without the third-party engine that is enabled in the standard edition, and has been achieving certification fairly reliably over the last year or so. In look and feel it's not much different, with the same shiny, colourful interface. Stability this time was perfect, with no problems observed. Scanning speeds were a little faster than the mainline product, while once again on-read protection was largely absent. Our set of activities was minimally impacted, and resource use was low.
Detection figures are absent thanks to the developers requesting to be excluded from the RAP test, but the core certification sets were handled properly and a VB100 award is earned.
TrustPort Antivirus 2016
Main version: 16.02.5698
Update versions: 16.0.2.5705
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 9 passed, 0 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 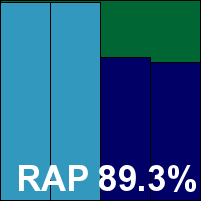 |
TrustPort's products have been stalwarts of our tests for many years now and can usually be relied upon to produce excellent detection levels thanks to their multi-engine approach. This month, the GUI came in a fairly attractive pale blue, with some nice clear information on the surface and a good set of options under the hood.
Stability was dented by a single incident while scanning some clean files, bringing up an API error message but not apparently affecting the actual scan. Scanning speeds were a little slow, file read overheads fairly high at first but showing some serious improvement later on. Detection was excellent, with a little drop into the proactive sets, and another perfect run through the certification sets earns TrustPort a VB100 award.
Results tables
| Product information | Install time (m)* | Reboot required | Fully 64-bit | Third-party engine technology§ | Stability score | Stability rating |
| AhnLab V3Net for Windows Server | 5:45 | √ | X | 1 | Stable | |
| Avast Business Security | 5:15 | √ | √ | 2.5 | Stable | |
| Avira Antivirus Server | 6:45 | X | X | 0 | Solid | |
| Bitdefender Endpoint Security | 7:00 | √ | X | 2.5 | Stable | |
| CYREN Command Anti-Malware | 3:30 | √ | X | 4.0 | Stable | |
| Defenx Security Suite | 3:00 | √ | X | K7 | 0 | Solid |
| eScan Internet Security Suite Server Edition | 11:45 | X | X | Bitdefender | 3 | Stable |
| ESET Endpoint Antivirus | 4:45 | √ | X | 0 | Solid | |
| ESTsoft ALYac | 13:00 | √ | X | Bitdefender | 1 | Stable |
| Fortinet FortiClient | 4:30 | X | X | 6 | Fair | |
| G DATA Antivirus Business | 48:45 | X | X | Bitdefender | 0 | Solid |
| Ikarus anti.virus | 2:00 | X | X | 0 | Solid | |
| K7 Total Security | 1:30 | X | X | 1 | Stable | |
| Kaspersky Anti-Virus 10 for Windows Servers | 4:15 | X | X | 0 | Solid | |
| NANO Antivirus Pro | 11:15 | X | X | 0 | Solid | |
| PC Pitstop PC Matic Home Security | 3:30 | X | X | 20 | Buggy | |
| Quick Heal AntiVirus Server Edition | 28:15 | √ | X | 3 | Stable | |
| Quick Heal Seqrite Antivirus Server Edition | 26:00 | √ | X | 1 | Stable | |
| Tencent PC Manager | 19:00 | X | X | Bitdefender | 2 | Stable |
| Tencent PC Manager - TAV | 2:45 | X | X | 0 | Solid | |
| TrustPort Antivirus 2016 | 11:45 | X | √ | Bitdefender | 1 | Stable |
0 = Solid 0.1 – 4.9 = Stable 5 – 14.9 = Fair 15 – 29.9 = Buggy 30+ = Flaky
* Install time includes initial updates and time to enable on-access protection (assuming reasonable typing speed and familiarity with product operation)
§ Only records presence of third-party scanning engines, most products will include additional in-house technologies
| Archive scanning | ACE | CAB | EXE-RAR | EXE-ZIP | JAR | LZH | RAR | TGZ | ZIP | 7z | TBZ2 | ZIPX | EXT* | |
| AhnLab V3Net for Windows Server | OD | 1 | 5 | X | X | 5 | X | 1 | 2 | 1 | 1 | 1 | 1 | √ |
| OA | X | X | X | X | X | X | X | X | X | X | X | X | √ | |
| Avast Business Security | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | X/√ | X/√ | 1/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | |
| Avira Antivirus Server | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | |
| Bitdefender Endpoint Security | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | X | X | X | X | 1 | X | X | X | 1 | X | X | 1 | √ | |
| CYREN Command Anti-Malware | OD | 5 | 5 | 5 | 5 | 5 | √ | 5 | 2 | 5 | 3 | 2 | 5 | √ |
| OA | 2/4 | 2/4 | 2/4 | 2/4 | 2/4 | √ | 2/4 | 1/2 | 2/4 | 1/1 | 1/2 | 2/4 | √ | |
| Defenx Security Suite | OD | √ | √ | X | X | √ | X | √ | X | √ | √ | X | √ | √ |
| OA | X | X | X | X | X | X | X | X | X | X | X | X | √ | |
| eScan Internet Security Suite Server Edition | OD | √ | X/√ | 5/8 | 5/8 | 7/√ | X/√ | X/√ | 5/8 | 1/√ | X/√ | X/8 | √ | √ |
| OA | √ | X/√ | X/√ | X/√ | √ | X/√ | X/√ | X/√ | 1/√ | X/√ | X/√ | X/√ | √ | |
| ESET Endpoint Antivirus | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | X | X | X | X | X | X | X | X | X | X | X | X | √ | |
| ESTsoft ALYac | OD | √ | √ | X | X | X | X | √ | X | X | √ | X | X | √ |
| OA | √ | √ | X | X | 1 | X | √ | X | 1 | √ | X | X | √ | |
| Fortinet FortiClient | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | √ | X | √ | √ | √ | X | X | X | X | X | √ | √ | √ | |
| G DATA Antivirus Business | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | 3/√ | 2/√ | √ | √ | 2/√ | 3/√ | 3/√ | 1/8 | 2/√ | 2/√ | 1/8 | 2/√ | √ | |
| Ikarus anti.virus | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | |
| K7 Total Security | OD | √ | √ | √ | √ | √ | X | √ | X | √ | √ | X | √ | √ |
| OA | X | X | X | X | X | X | X | X | X | X | X | X | √ | |
| Kaspersky Anti-Virus 10 for Windows Servers | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | X/√ | X/√ | √ | √ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | X/√ | √ | |
| NANO Antivirus Pro | OD | 8/√ | 8/√ | 4/√ | 4/√ | 8/√ | X | 8/√ | 4/√ | 8/√ | 8/√ | 4/√ | 8/√ | √ |
| OA | X | X | X | X | X | X | X | X | X | X | X | X | √ | |
| PC Pitstop PC Matic Home Security | OD | X | X | √ | √ | X | X | X | X | X | X | X | X | X |
| OA | X | X | √ | √ | X | X | X | X | X | X | X | X | X | |
| Quick Heal AntiVirus Server Edition | OD | 2/5 | X/5 | 2/2 | 2/2 | 2/5 | 3/6 | 2/5 | X/2 | 2/5 | 2/5 | X/2 | 2/5 | √ |
| OA | X | X | X | X | 1 | X | X | X | 1 | X | X | X | √ | |
| Quick Heal Seqrite Antivirus Server Edition | OD | 2/5 | X/5 | 2/2 | 2/2 | 2/5 | 3/6 | 2/5 | X/2 | 2/5 | 2/5 | X/2 | 2/5 | √ |
| OA | X | X | X | X | 1 | X | X | X | 1 | X | X | X | √ | |
| Tencent PC Manager | OD | √ | √ | 7 | 7 | √ | √ | √ | 7 | √ | √ | 7 | √ | √ |
| OA | X/2 | X/2 | X/1 | X/1 | X/2 | X/2 | X/2 | X/1 | X/2 | X/2 | X/1 | X/2 | 1/√ | |
| Tencent PC Manager - TAV | OD | √ | √ | √ | √ | √ | X | √ | √ | √ | √ | X | √ | √ |
| OA | X/√ | X/√ | X/√ | X/√ | X/√ | X | X/√ | X/√ | X/√ | X/√ | X | X/√ | 1/√ | |
| TrustPort Antivirus 2016 | OD | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| OA | √ | √ | 7/√ | 8/√ | 1/√ | √ | √ | √ | 1/√ | √ | √ | 1/√ | √ |
Key:
√ - Detection of EICAR test file up to ten levels of nesting
X - No detection of EICAR test file
X/√ - default settings/all files
1-9 - Detection of EICAR test file up to specified nesting level
If just z-exe detection in ext, then X
*Detection of EICAR test file with randomly chosen file extension
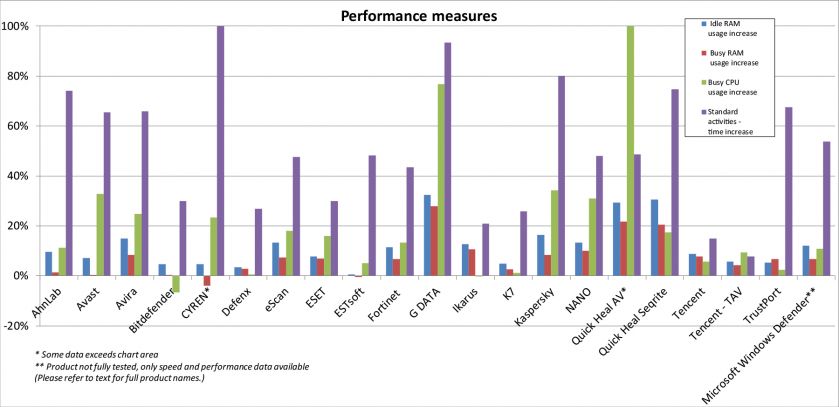
| Performance measures | Idle RAM usage increase | Busy RAM usage increase | Busy CPU usage increase | Standard activities - time increase |
| AhnLab V3Net for Windows Server | 9.52% | 1.45% | 11.26% | 74.17% |
| Avast Business Security | 7.16% | 0.31% | 32.84% | 65..52% |
| Avira Antivirus Server | 14.90% | 8.32% | 24.89% | 65.88% |
| Bitdefender Endpoint Security | 4.78% | 0.34% | -6.56% | 30.02% |
| CYREN Command Anti-Malware | 4.72% | -3.97% | 23.40% | 523.69% |
| Defenx Security Suite | 3.41% | 2.75% | 0.62% | 26.84% |
| eScan Internet Security Suite Server Edition | 13.27% | 7.31% | 18.09% | 47.64% |
| ESET Endpoint Antivirus | 7.75% | 6.86% | 15.90% | 29.84% |
| ESTsoft ALYac | 0.49% | -0.42% | 5.10% | 48.23% |
| Fortinet FortiClient | 11.38% | 6.70% | 13.24% | 43.42% |
| G DATA Antivirus Business | 32.47% | 27.82% | 76.70% | 93.38% |
| Ikarus anti.virus | 12.65% | 10.64% | -0.19% | 20.84% |
| K7 Total Security | 4.78% | 2.71% | 1.22% | 25.87% |
| Kaspersky Anti-Virus 10 for Windows Servers | 16.37% | 8.31% | 34.22% | 80.13% |
| NANO Antivirus Pro | 13.26% | 10.06% | 30.88% | 47.93% |
| PC Pitstop PC Matic Home Security | N/T | N/T | N/T | N/T |
| Quick Heal AntiVirus Server Edition | 29.28% | 21.62% | 105.07% | 48.54% |
| Quick Heal Seqrite Antivirus Server Edition | 30.53% | 20.59% | 17.49% | 74.68% |
| Tencent PC Manager | 8.84% | 7.69% | 5.69% | 14.88% |
| Tencent PC Manager - TAV | 5.65% | 4.19% | 9.48% | 7.82% |
| TrustPort Antivirus 2016 | 5.24% | 6.65% | 2.44% | 67.44% |
| Microsoft Windows Defender* | 11.99% | 6.65% | 10.83% | 53.85% |
*Product not fully tested, only speed and performance data available. N/T = Not tested.
| On-demand throughput (MB/s) | System drive* | Archive files | Binaries and system files | Media and documents | Other file types | ||||||||
| Default (cold) | Default (warm) | All files | Default (cold) | Default (warm) | All files | Default (cold) | Default (warm) | All files | Default (cold) | Default (warm) | All files | ||
| AhnLab V3Net for Windows Server | 97.62 | 7.78 | 5.47 | N/A | 6.69 | 9.70 | 6.69 | 14.16 | 14.16 | 14.16 | 11.12 | 15.54 | 11.12 |
| Avast Business Security | 10.88 | 2.30 | 2.39 | 2.30 | 3.18 | 2.98 | 3.18 | 11.30 | 11.08 | 11.30 | 8.83 | 7.58 | 8.83 |
| Avira Antivirus Server | 8.15 | 9.15 | 7.32 | 9.15 | 4.21 | 4.34 | 4.21 | 8.94 | 10.03 | 8.94 | 7.83 | 8.20 | 7.83 |
| Bitdefender Endpoint Security | 38.17 | 13.49 | 1366.06 | 13.49 | 9.51 | 3157.44 | 9.51 | 13.95 | 1429.88 | 13.95 | 15.19 | 1906.56 | 15.19 |
| CYREN Command Anti-Malware | 3.87 | 3.56 | 3.35 | 3.56 | 1.57 | 2.15 | 1.57 | 4.17 | 6.51 | 4.17 | 4.46 | 6.17 | 4.46 |
| Defenx Security Suite | 24.56 | 8.88 | 546.34 | 8.88 | 3.88 | 420.99 | 3.88 | 8.41 | 268.12 | 8.41 | 5.34 | 224.30 | 5.34 |
| eScan Internet Security Suite | 13.74 | 44.41 | 86.71 | 14.57 | 8.08 | 36.15 | 7.61 | 9.83 | 31.66 | 12.33 | |||
K7computing : Security Vulnerabilities
| # | CVE ID | CWE ID | # of Exploits | Vulnerability Type(s) | Publish Date | Update Date | Score | Gained Access Level | Access | Complexity | Authentication | Conf. | Integ. | Avail. | |||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | CVE-2018-5220 | 20 | DoS | 2018-01-04 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 Antivirus 15.1.0306, the driver file (K7Sentry.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x95002610. | |||||||||||||||||||
| 2 | CVE-2018-5219 | 20 | DoS | 2018-01-04 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 Antivirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x83002168. | |||||||||||||||||||
| 3 | CVE-2018-5218 | 20 | DoS | 2018-01-04 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 Antivirus 15.1.0306, the driver file (K7Sentry.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x950025b0. | |||||||||||||||||||
| 4 | CVE-2018-5217 | 20 | DoS | 2018-01-04 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 Antivirus 15.1.0306, the driver file (K7Sentry.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x95002578. | |||||||||||||||||||
| 5 | CVE-2018-5088 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x8300211C. | |||||||||||||||||||
| 6 | CVE-2018-5087 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x83002100. | |||||||||||||||||||
| 7 | CVE-2018-5086 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x8300215F. | |||||||||||||||||||
| 8 | CVE-2018-5085 | 20 | DoS | 2018-01-03 | 2018-01-12 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x83002124. | |||||||||||||||||||
| 9 | CVE-2018-5084 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x8300212C. | |||||||||||||||||||
| 10 | CVE-2018-5083 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x8300215B. | |||||||||||||||||||
| 11 | CVE-2018-5082 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x83002128. | |||||||||||||||||||
| 12 | CVE-2018-5081 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x830020F0. | |||||||||||||||||||
| 13 | CVE-2018-5080 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x830020FC. | |||||||||||||||||||
| 14 | CVE-2018-5079 | 20 | DoS | 2018-01-03 | 2018-01-11 | None | Local | Low | Not required | Partial | Partial | Complete | |||||||
| In K7 AntiVirus 15.1.0306, the driver file (K7FWHlpr.sys) allows local users to cause a denial of service (BSOD) or possibly have unspecified other impact because of not validating input values from IOCtl 0x83002130. | |||||||||||||||||||
| 15 | CVE-2017-18019 | 20 | 2018-01-03 | 2018-01-19 | None | Local | Low | Not required | Partial | None | Partial | ||||||||
| In K7 Total Security before 15.1.0.305, user-controlled input to the K7Sentry device is not sufficiently sanitized: the user-controlled input can be used to compare an arbitrary memory address with a fixed value, which in turn can be used to read the contents of arbitrary memory. Similarly, the product crashes upon a \\.\K7Sentry DeviceIoControl call with an invalid kernel pointer. | |||||||||||||||||||
| 16 | CVE-2017-17701 | 476 | 2017-12-15 | 2017-12-20 | None | Remote | Low | Not required | Partial | Partial | Partial | ||||||||
| K7Sentry.sys 15.1.0.59 in K7 Antivirus 15.1.0309 has a NULL pointer dereference via a 0x950025c8 DeviceIoControl request. | |||||||||||||||||||
| 17 | CVE-2017-17700 | 476 | 2017-12-15 | 2017-12-20 | None | Remote | Low | Not required | Partial | Partial | Partial | ||||||||
| K7Sentry.sys 15.1.0.59 in K7 Antivirus 15.1.0309 has a NULL pointer dereference via a 0x950025a4 DeviceIoControl request. | |||||||||||||||||||
| 18 | CVE-2017-17699 | 476 | 2017-12-15 | 2017-12-20 | None | Remote | Low | Not required | Partial | Partial | Partial | ||||||||
| K7Sentry.sys 15.1.0.59 in K7 Antivirus 15.1.0309 has a NULL pointer dereference via a 0x950025ac DeviceIoControl request. | |||||||||||||||||||
| 19 | CVE-2017-17465 | 476 | 2017-12-08 | 2017-12-20 | None | Remote | Low | Not required | Partial | Partial | Partial | ||||||||
| K7Sentry.sys 15.1.0.59 in K7 Antivirus 15.1.0309 has a NULL pointer dereference via a 0x95002574 DeviceIoControl request. | |||||||||||||||||||
| 20 | CVE-2017-17464 | 476 | 2017-12-08 | 2017-12-20 | None | Remote | Low | Not required | Partial | Partial | Partial | ||||||||
| K7Sentry.sys 15.1.0.59 in K7 Antivirus 15.1.0309 has a NULL pointer dereference via a 0x95002570 DeviceIoControl request. | |||||||||||||||||||
| 21 | CVE-2017-17429 | 20 | 2018-01-16 | 2019-10-02 | None | Local | Low | Not required | Partial | None | None | ||||||||
| In K7 Antivirus Premium before 15.1.0.53, user-controlled input to the K7Sentry device is not sufficiently authenticated: a local user with a LOW integrity process can access a raw hard disk by sending a specific IOCTL. | |||||||||||||||||||
| 22 | CVE-2017-16557 | 787 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Medium | Not required | Partial | Partial | Partial | |||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to gain privileges by sending a specific IOCTL after setting the memory in a particular way. | |||||||||||||||||||
| 23 | CVE-2017-16555 | 787 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Medium | Not required | Partial | Partial | Partial | |||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to gain privileges by sending a specific IOCTL after setting the memory in a particular way. | |||||||||||||||||||
| 24 | CVE-2017-16554 | 787 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Low | Not required | Partial | Partial | Partial | |||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to write to arbitrary memory locations, and consequently gain privileges, via a specific set of IOCTL calls. | |||||||||||||||||||
| 25 | CVE-2017-16553 | 787 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Medium | Not required | Partial | Partial | Partial | |||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to gain privileges by sending a specific IOCTL after setting the memory in a particular way. | |||||||||||||||||||
| 26 | CVE-2017-16552 | 787 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Low | Not required | Partial | Partial | Partial | |||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to write to arbitrary memory locations, and consequently gain privileges, via a specific set of IOCTL calls. | |||||||||||||||||||
| 27 | CVE-2017-16551 | 787 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Medium | Not required | Partial | Partial | Partial | |||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to gain privileges by sending a specific IOCTL after setting the memory in a particular way. | |||||||||||||||||||
| 28 | CVE-2017-16550 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Low | Not required | Partial | Partial | Partial | ||||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to write to arbitrary memory locations, and consequently gain privileges, via a specific set of IOCTL calls. | |||||||||||||||||||
| 29 | CVE-2017-16549 | 787 | +Priv | 2018-01-16 | 2019-10-02 | None | Local | Low | Not required | Partial | Partial | Partial | |||||||
| K7 Antivirus Premium before 15.1.0.53 allows local users to write to arbitrary memory locations, and consequently gain privileges, via a specific set of IOCTL calls. | |||||||||||||||||||
| 30 | CVE-2014-9643 | 264 | 1 | +Priv | 2015-02-06 | 2015-02-09 | None | Local | Low | Not required | Complete | Complete | Complete | ||||||
| K7Sentry.sys in K7 Computing Ultimate Security, Anti-Virus Plus, and Total Security before 14.2.0.253 allows local users to write to arbitrary memory locations, and consequently gain privileges, via a crafted 0x95002570, 0x95002574, 0x95002580, 0x950025a8, 0x950025ac, or 0x950025c8 IOCTL call. | |||||||||||||||||||
| 31 | CVE-2014-8956 | 119 | Exec Code Overflow | 2014-12-12 | 2014-12-15 | None | Local | Low | Not required | Complete | Complete | Complete | |||||||
| Stack-based buffer overflow in the K7Sentry.sys kernel mode driver (aka K7AV Sentry Device Driver) before 12.8.0.119, as used in multiple K7 Computing products, allows local users to execute arbitrary code with kernel privileges via unspecified vectors. | |||||||||||||||||||
| 32 | CVE-2014-8608 | DoS | 2014-12-12 | 2016-12-15 | None | Local | Low | Not required | None | None | Complete | ||||||||
| The K7Sentry.sys kernel mode driver (aka K7AV Sentry Device Driver) before 12.8.0.119, as used in multiple K7 Computing products, allows local users to cause a denial of service (NULL pointer dereference) as demonstrated by a filename containing "crashme$$". | |||||||||||||||||||
| 33 | CVE-2014-7136 | 119 | Exec Code Overflow | 2014-12-12 | 2014-12-15 | None | Local | Low | Not required | Complete | Complete | Complete | |||||||
| Heap-based buffer overflow in the K7FWFilt.sys kernel mode driver (aka K7Firewall Packet Driver) before 14.0.1.16, as used in multiple K7 Computing products, allows local users to execute arbitrary code with kernel privileges via a crafted parameter in a DeviceIoControl API call. | |||||||||||||||||||
| 34 | CVE-2012-1461 | 264 | Bypass | 2012-03-21 | 2012-11-06 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The Gzip file parser in AVG Anti-Virus 10.0.0.1190, Bitdefender 7.2, Command Antivirus 5.2.11.5, Emsisoft Anti-Malware 5.1.0.1, F-Secure Anti-Virus 9.0.16160.0, Fortinet Antivirus 4.2.254.0, Ikarus Virus Utilities T3 Command Line Scanner 1.1.97.0, Jiangmin Antivirus 13.0.900, K7 AntiVirus 9.77.3565, Kaspersky Anti-Virus 7.0.0.125, McAfee Anti-Virus Scanning Engine 5.400.0.1158, McAfee Gateway (formerly Webwasher) 2010.1C, NOD32 Antivirus 5795, Norman Antivirus 6.06.12, Rising Antivirus 22.83.00.03, Sophos Anti-Virus 4.61.0, AVEngine 20101.3.0.103 in Symantec Endpoint Protection 11, Trend Micro AntiVirus 9.120.0.1004, Trend Micro HouseCall 9.120.0.1004, and VBA32 3.12.14.2 allows remote attackers to bypass malware detection via a .tar.gz file with multiple compressed streams. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different Gzip parser implementations. | |||||||||||||||||||
| 35 | CVE-2012-1460 | 264 | Bypass | 2012-03-21 | 2017-08-28 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The Gzip file parser in Antiy Labs AVL SDK 2.0.3.7, Quick Heal (aka Cat QuickHeal) 11.00, Command Antivirus 5.2.11.5, eSafe 7.0.17.0, F-Prot Antivirus 4.6.2.117, Jiangmin Antivirus 13.0.900, K7 AntiVirus 9.77.3565, and VBA32 3.12.14.2 allows remote attackers to bypass malware detection via a .tar.gz file with stray bytes at the end. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different Gzip parser implementations. | |||||||||||||||||||
| 36 | CVE-2012-1459 | 264 | Bypass | 2012-03-21 | 2018-01-17 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The TAR file parser in AhnLab V3 Internet Security 2011.01.18.00, Avira AntiVir 7.11.1.163, Antiy Labs AVL SDK 2.0.3.7, avast! Antivirus 4.8.1351.0 and 5.0.677.0, AVG Anti-Virus 10.0.0.1190, Bitdefender 7.2, Quick Heal (aka Cat QuickHeal) 11.00, ClamAV 0.96.4, Command Antivirus 5.2.11.5, Comodo Antivirus 7424, Emsisoft Anti-Malware 5.1.0.1, F-Prot Antivirus 4.6.2.117, F-Secure Anti-Virus 9.0.16160.0, Fortinet Antivirus 4.2.254.0, G Data AntiVirus 21, Ikarus Virus Utilities T3 Command Line Scanner 1.1.97.0, Jiangmin Antivirus 13.0.900, K7 AntiVirus 9.77.3565, Kaspersky Anti-Virus 7.0.0.125, McAfee Anti-Virus Scanning Engine 5.400.0.1158, McAfee Gateway (formerly Webwasher) 2010.1C, Antimalware Engine 1.1.6402.0 in Microsoft Security Essentials 2.0, NOD32 Antivirus 5795, Norman Antivirus 6.06.12, nProtect Anti-Virus 2011-01-17.01, Panda Antivirus 10.0.2.7, PC Tools AntiVirus 7.0.3.5, Rising Antivirus 22.83.00.03, Sophos Anti-Virus 4.61.0, AVEngine 20101.3.0.103 in Symantec Endpoint Protection 11, Trend Micro AntiVirus 9.120.0.1004, Trend Micro HouseCall 9.120.0.1004, VBA32 3.12.14.2, and VirusBuster 13.6.151.0 allows remote attackers to bypass malware detection via a TAR archive entry with a length field corresponding to that entire entry, plus part of the header of the next entry. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different TAR parser implementations. | |||||||||||||||||||
| 37 | CVE-2012-1457 | 264 | Bypass | 2012-03-21 | 2018-01-17 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The TAR file parser in Avira AntiVir 7.11.1.163, Antiy Labs AVL SDK 2.0.3.7, avast! Antivirus 4.8.1351.0 and 5.0.677.0, AVG Anti-Virus 10.0.0.1190, Bitdefender 7.2, Quick Heal (aka Cat QuickHeal) 11.00, ClamAV 0.96.4, Command Antivirus 5.2.11.5, Emsisoft Anti-Malware 5.1.0.1, eSafe 7.0.17.0, F-Prot Antivirus 4.6.2.117, G Data AntiVirus 21, Ikarus Virus Utilities T3 Command Line Scanner 1.1.97.0, Jiangmin Antivirus 13.0.900, K7 AntiVirus 9.77.3565, Kaspersky Anti-Virus 7.0.0.125, McAfee Anti-Virus Scanning Engine 5.400.0.1158, McAfee Gateway (formerly Webwasher) 2010.1C, Antimalware Engine 1.1.6402.0 in Microsoft Security Essentials 2.0, NOD32 Antivirus 5795, Norman Antivirus 6.06.12, PC Tools AntiVirus 7.0.3.5, Rising Antivirus 22.83.00.03, AVEngine 20101.3.0.103 in Symantec Endpoint Protection 11, Trend Micro AntiVirus 9.120.0.1004, Trend Micro HouseCall 9.120.0.1004, VBA32 3.12.14.2, and VirusBuster 13.6.151.0 allows remote attackers to bypass malware detection via a TAR archive entry with a length field that exceeds the total TAR file size. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different TAR parser implementations. | |||||||||||||||||||
| 38 | CVE-2012-1443 | 264 | Bypass | 2012-03-21 | 2012-11-06 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The RAR file parser in ClamAV 0.96.4, Rising Antivirus 22.83.00.03, Quick Heal (aka Cat QuickHeal) 11.00, G Data AntiVirus 21, AVEngine 20101.3.0.103 in Symantec Endpoint Protection 11, Command Antivirus 5.2.11.5, Ikarus Virus Utilities T3 Command Line Scanner 1.1.97.0, Emsisoft Anti-Malware 5.1.0.1, PC Tools AntiVirus 7.0.3.5, F-Prot Antivirus 4.6.2.117, VirusBuster 13.6.151.0, Fortinet Antivirus 4.2.254.0, Antiy Labs AVL SDK 2.0.3.7, K7 AntiVirus 9.77.3565, Trend Micro HouseCall 9.120.0.1004, Kaspersky Anti-Virus 7.0.0.125, Jiangmin Antivirus 13.0.900, Antimalware Engine 1.1.6402.0 in Microsoft Security Essentials 2.0, Sophos Anti-Virus 4.61.0, NOD32 Antivirus 5795, Avira AntiVir 7.11.1.163, Norman Antivirus 6.06.12, McAfee Anti-Virus Scanning Engine 5.400.0.1158, Panda Antivirus 10.0.2.7, McAfee Gateway (formerly Webwasher) 2010.1C, Trend Micro AntiVirus 9.120.0.1004, Comodo Antivirus 7424, Bitdefender 7.2, eSafe 7.0.17.0, F-Secure Anti-Virus 9.0.16160.0, nProtect Anti-Virus 2011-01-17.01, AhnLab V3 Internet Security 2011.01.18.00, AVG Anti-Virus 10.0.0.1190, avast! Antivirus 4.8.1351.0 and 5.0.677.0, and VBA32 3.12.14.2 allows user-assisted remote attackers to bypass malware detection via a RAR file with an initial MZ character sequence. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different RAR parser implementations. | |||||||||||||||||||
| 39 | CVE-2012-1426 | 264 | Bypass | 2012-03-21 | 2017-08-28 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The TAR file parser in Quick Heal (aka Cat QuickHeal) 11.00, Command Antivirus 5.2.11.5, F-Prot Antivirus 4.6.2.117, K7 AntiVirus 9.77.3565, Norman Antivirus 6.06.12, and Rising Antivirus 22.83.00.03 allows remote attackers to bypass malware detection via a POSIX TAR file with an initial \42\5A\68 character sequence. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different TAR parser implementations. | |||||||||||||||||||
| 40 | CVE-2012-1423 | 264 | Bypass | 2012-03-21 | 2012-08-13 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The TAR file parser in Command Antivirus 5.2.11.5, Emsisoft Anti-Malware 5.1.0.1, F-Prot Antivirus 4.6.2.117, Fortinet Antivirus 4.2.254.0, Ikarus Virus Utilities T3 Command Line Scanner 1.1.97.0, K7 AntiVirus 9.77.3565, NOD32 Antivirus 5795, Norman Antivirus 6.06.12, PC Tools AntiVirus 7.0.3.5, Rising Antivirus 22.83.00.03, and VirusBuster 13.6.151.0 allows remote attackers to bypass malware detection via a POSIX TAR file with an initial MZ character sequence. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different TAR parser implementations. | |||||||||||||||||||
| 41 | CVE-2012-1420 | 264 | Bypass | 2012-03-21 | 2012-08-13 | None | Remote | Medium | Not required | None | Partial | None | |||||||
| The TAR file parser in Quick Heal (aka Cat QuickHeal) 11.00, Command Antivirus 5.2.11.5, F-Prot Antivirus 4.6.2.117, Fortinet Antivirus 4.2.254.0, K7 AntiVirus 9.77.3565, Kaspersky Anti-Virus 7.0.0.125, Antimalware Engine 1.1.6402.0 in Microsoft Security Essentials 2.0, NOD32 Antivirus 5795, Norman Antivirus 6.06.12, Panda Antivirus 10.0.2.7, and Rising Antivirus 22.83.00.03 allows remote attackers to bypass malware detection via a POSIX TAR file with an initial \7fELF character sequence. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different TAR parser implementations. | |||||||||||||||||||
| 42 | CVE-2008-5533 | 20 | Bypass | 2008-12-12 | 2018-10-11 | None | Remote | Medium | Not required | Complete | Complete | Complete | |||||||
| K7AntiVirus 7.10.541 and possibly 7.10.454, when Internet Explorer 6 or 7 is used, allows remote attackers to bypass detection of malware in an HTML document by placing an MZ header (aka "EXE info") at the beginning, and modifying the filename to have (1) no extension, (2) a .txt extension, or (3) a .jpg extension, as demonstrated by a document containing a CVE-2006-5745 exploit. | |||||||||||||||||||
What’s New in the k7 total security 2016 Archives?
Screen Shot

System Requirements for K7 total security 2016 Archives
- First, download the K7 total security 2016 Archives
-
You can download its setup from given links:


